Securing non-human identities in AWS environments (and beyond)
Non-human identities (NHIs) such as IAM users, roles, service accounts, external keys, and secrets are crucial for accessing resources within AWS environments. However, managing and securing these identities presents unique challenges. In this article, we will cover how Astrix helps you with the toughest questions of identity security: what permissions NHIs have, to which resources, who is behind them, and the risks they pose in real-time. Let’s get to the details.
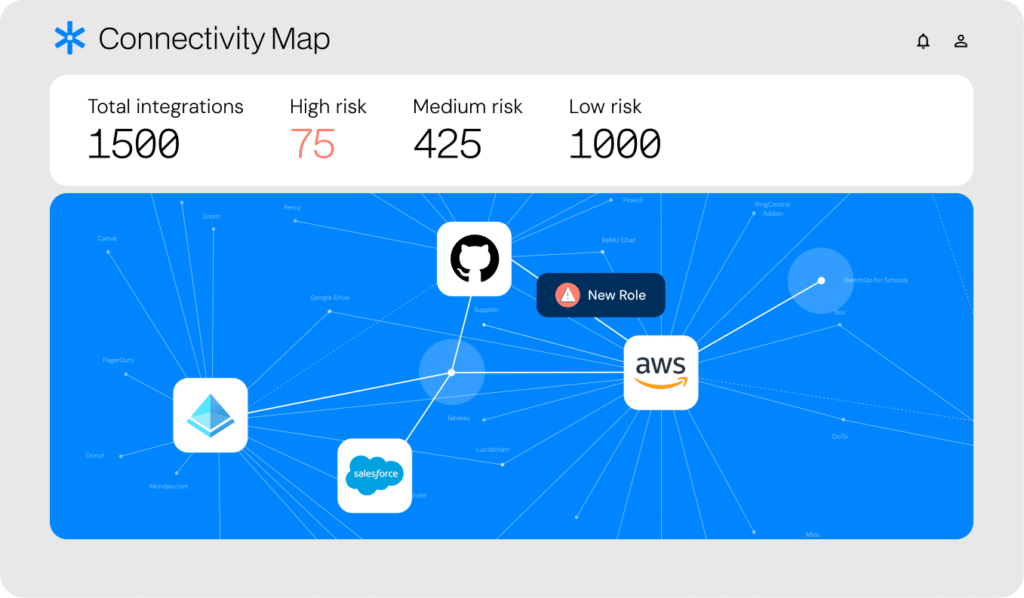
Visibility and discovery
Maintaining an accurate and up-to-date inventory of NHIs is a significant task. Astrix provides real-time discovery of all NHIs, mapping their interconnectivity within AWS and external platforms. This holistic visibility ensures you always understand who is behind each NHIs and how they are used, helping prevent unauthorized access.
Lifecycle management
Managing the lifecycle of NHIs from creation to decommissioning is challenging, to say the least. Astrix streamlines this process through policy-based attestation, automated alerts, and offboarding procedures. This ensures that NHIs are appropriately governed, reducing the risk of orphaned identities and permission creep.
Actionable risk modeling
Not all NHIs pose the same level of risk. Astrix provides actionable risk modeling by offering context into the services and resources an NHI can access, the permissions it holds, its usage patterns, and real-time behavior. This detailed analysis helps prioritize risks and focus on the most critical security issues, enabling more effective risk management and resource allocation.
Proactive threat detection
Astrix is the only NHI security solution that offers non-human ITDR capabilities. In addition to policy deviations and third-party vendor breach response (which we cover in detail in the next paragraph), Astrix’s AI-based threat engines identify suspicious NHI activity by analyzing parameters such as unusual IP addresses, user agents, and API activities – alerting when a threat is detected, and providing detailed investigation guides and activity logs.
Third-party breach response
“We recommend rotating all credentials.” Every security and engineering team dreads this sentence. Using Astrix, finding all credentials related to a breached third-party vendor is as easy as a click of a button. Astrix helps expedite incident response efforts by mapping every associated NHI, showing everything it’s connected to, and how it’s used. This allows you to easily remove or rotate compromised credentials, saving countless hours and minimizing potential risk.
Seamless integration with existing security tools
To wrap up, we will finish with some good ol’ automations – a security team’s best friend. Astrix integrates with your existing SIEM, SOAR, and ITSM systems to allow for automated notifications, ticket generation, and workflow management, ensuring that overhead is kept to a minimum and security operations do not disrupt business processes.
To learn more about securing non-human identities in AWS environments with Astrix, read the full solution brief, or schedule a demo.