Posture management
Identity and access management for the non-human layer is key for a tight security posture. From redundant tokens to over-permissive access – Astrix helps security teams easily reduce their non-human identity attack surface with rich security context, prioritization and out-of-the-box policies.
Maintain a tight security posture and easily remediate risks
Quickly improve your security posture with a prioritized list of NHI security issues. Remediate confidently, without breaking critical processes.
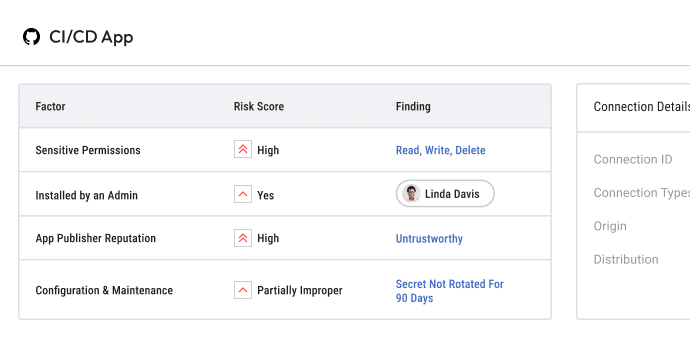
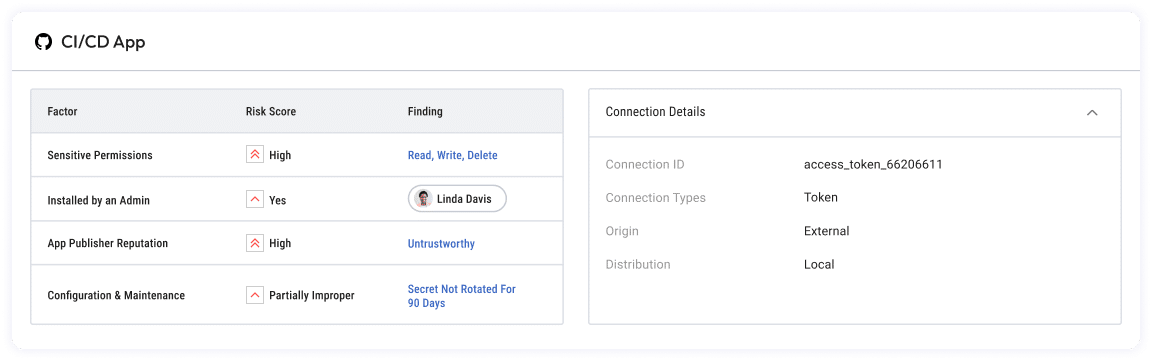
Risk & business context
- Remediate with confidence and prioritize risks using comprehensive risk and business context for each NHI.
- Get risk insights such as over-permissive access & scopes, redundant access and NHIs that haven’t been properly decommissioned.
- Get the business value of each NHI including usage and owners.
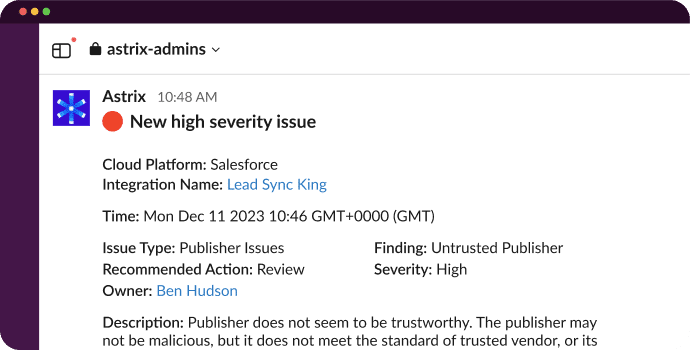
Digested and prioritized security alerts
- Get prioritized alerts that are ready for action.
- Use end-user feedback, threat context, severity level, and suggested remediation steps to accurately mitigate threats.
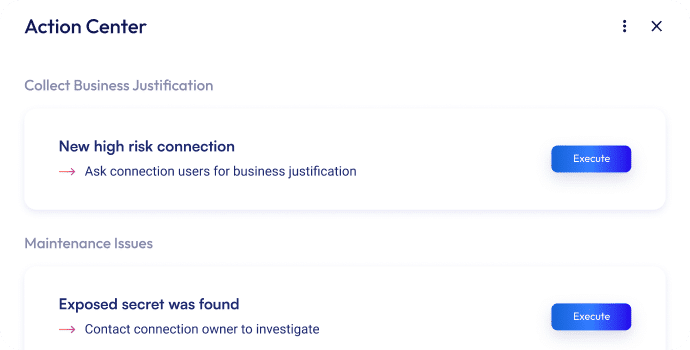
Easily remediate risks
- Make better decisions using automated workflows involving end-user feedback.
- Remediate in a click of a button with out-of-the-box policies and custom workflows.
Secure your non-human identities
Blog & News
Blog
News

Astrix Discovers 0-Day Vulnerability in Google Cloud Platform

Astrix Security Named a Finalist for RSA Conference 2023 Innovation Sandbox
Security Boulevard – Supply Chain Dependency: What Your GitHub Connections May Trigger

Astrix Security Named a Finalist for RSA Conference 2023 Innovation Sandbox