Astrix integrates with Slack
Astrix is now available on the Slack App Directory and enables enterprises to secure non-human identities in Slack environments leveraging AI detection capabilities. In addition, Astrix offers deeper integration with Slack, which enables customers to accelerate and streamline the remediation of non-human identity threats across additional core environments like Azure AD, Salesforce, AWS, Github, GCP, and more.
Astrix integrates with Slack to strengthen security for non-human identities across enterprises’ core systems like Slack, Microsoft Azure AD, Salesforce, AWS, GCP, GitHub, and more.
Employees increasingly connect third-party apps and GenAI tools to their organization’s core systems to increase productivity and streamline processes. Each of these connections grants powerful access keys to a third-party app or GenAI vendor. Additionally, engineering teams regularly create secrets that connect internal services and resources to “make stuff work”. These secrets are scattered all over different secret managers, with zero security visibility and context.
These two types of connections (internal and third-party) are done through non-human identities, which cannot be monitored by traditional identity and access (IAM) solutions, open an ungoverned attack surface that threat actors exploit to gain initial access, escalate privileges, and move laterally to steal sensitive data.
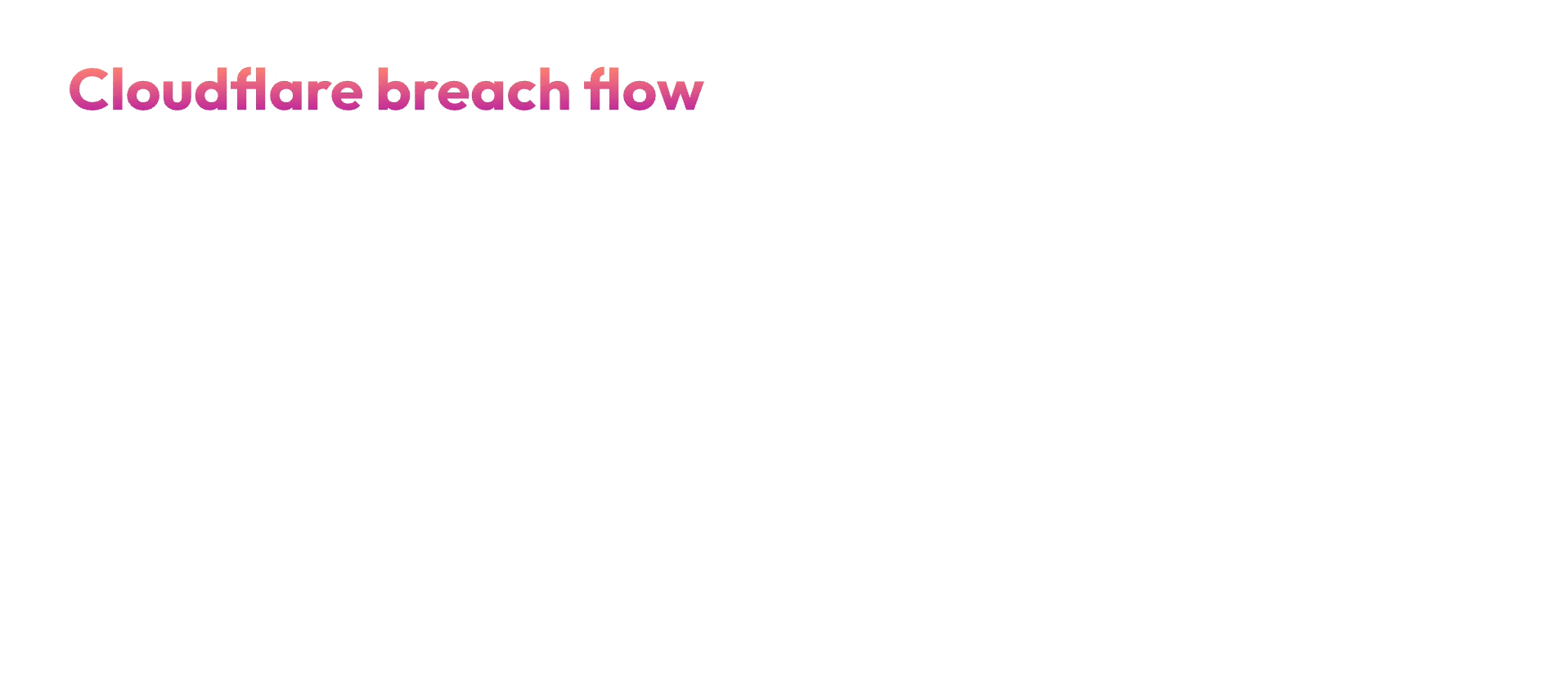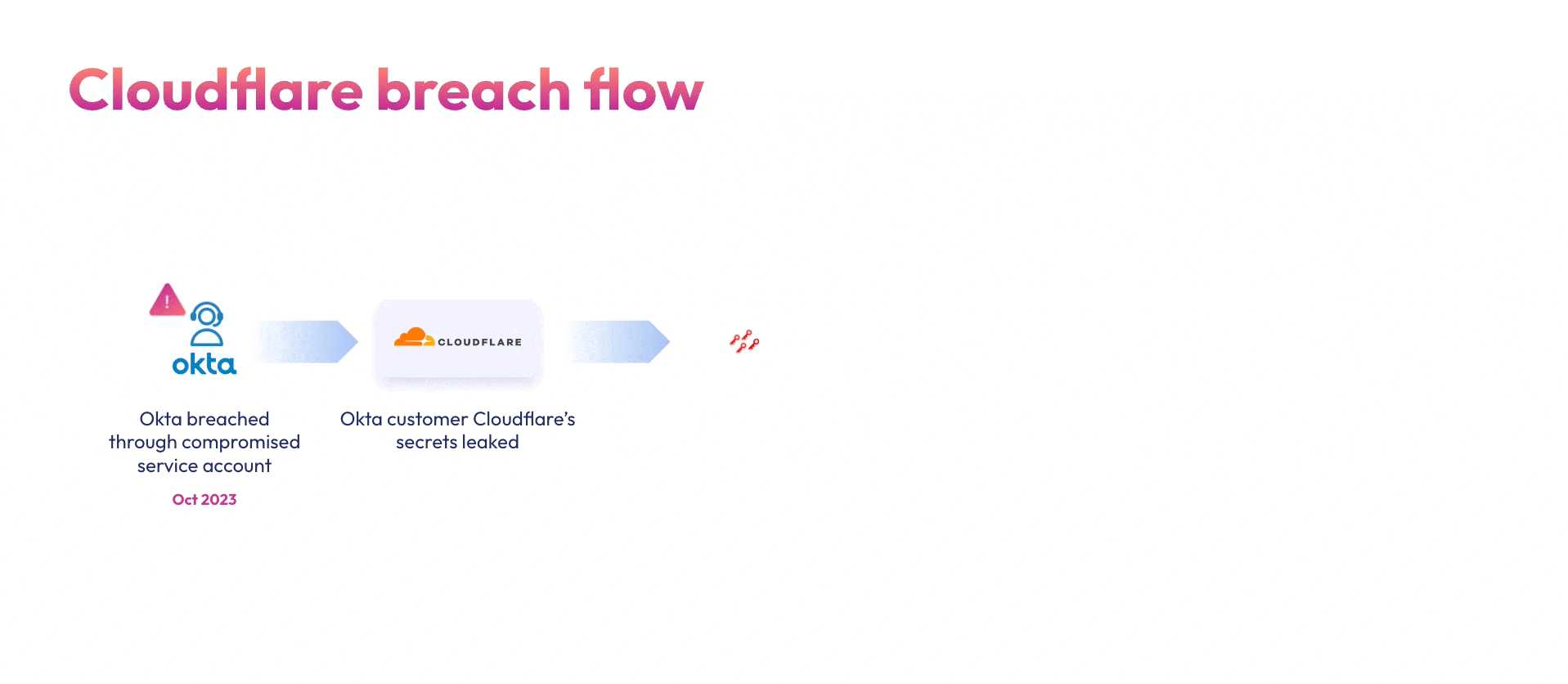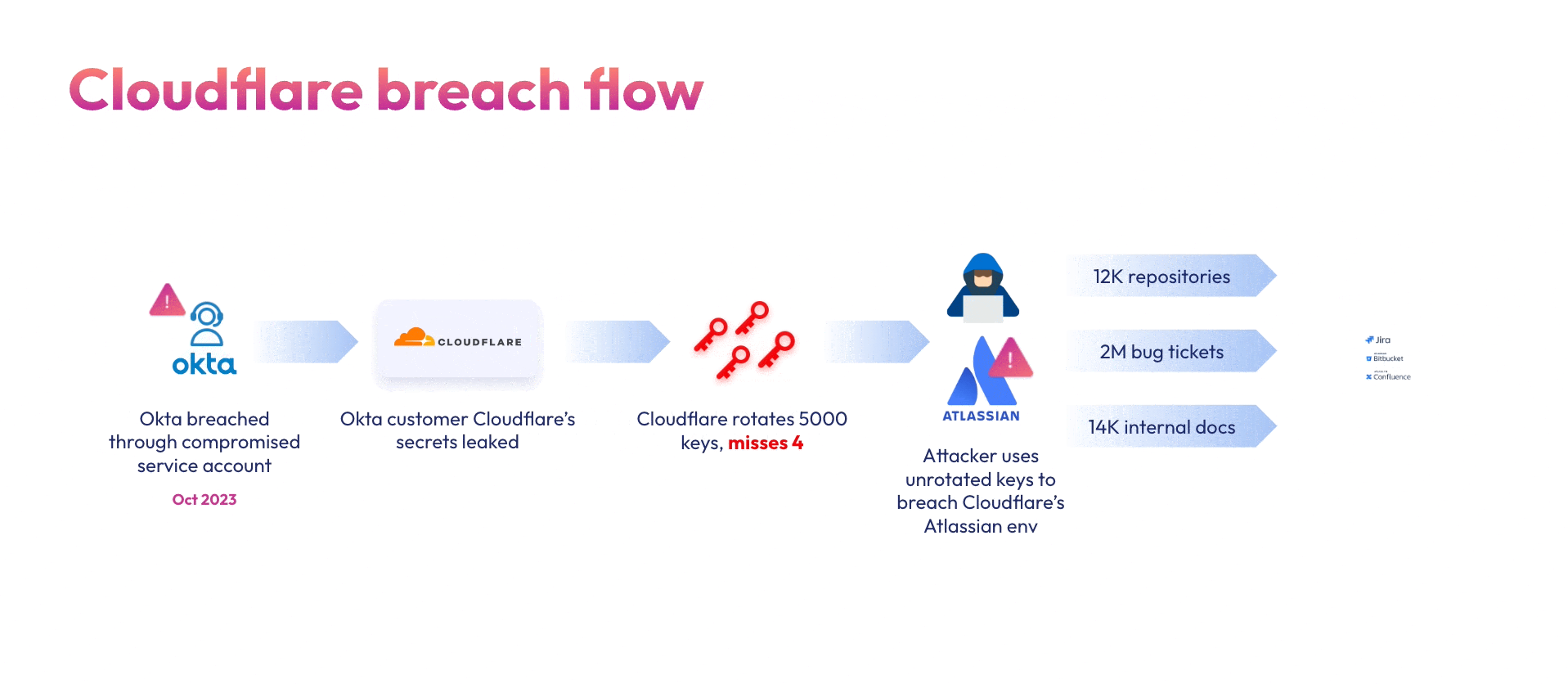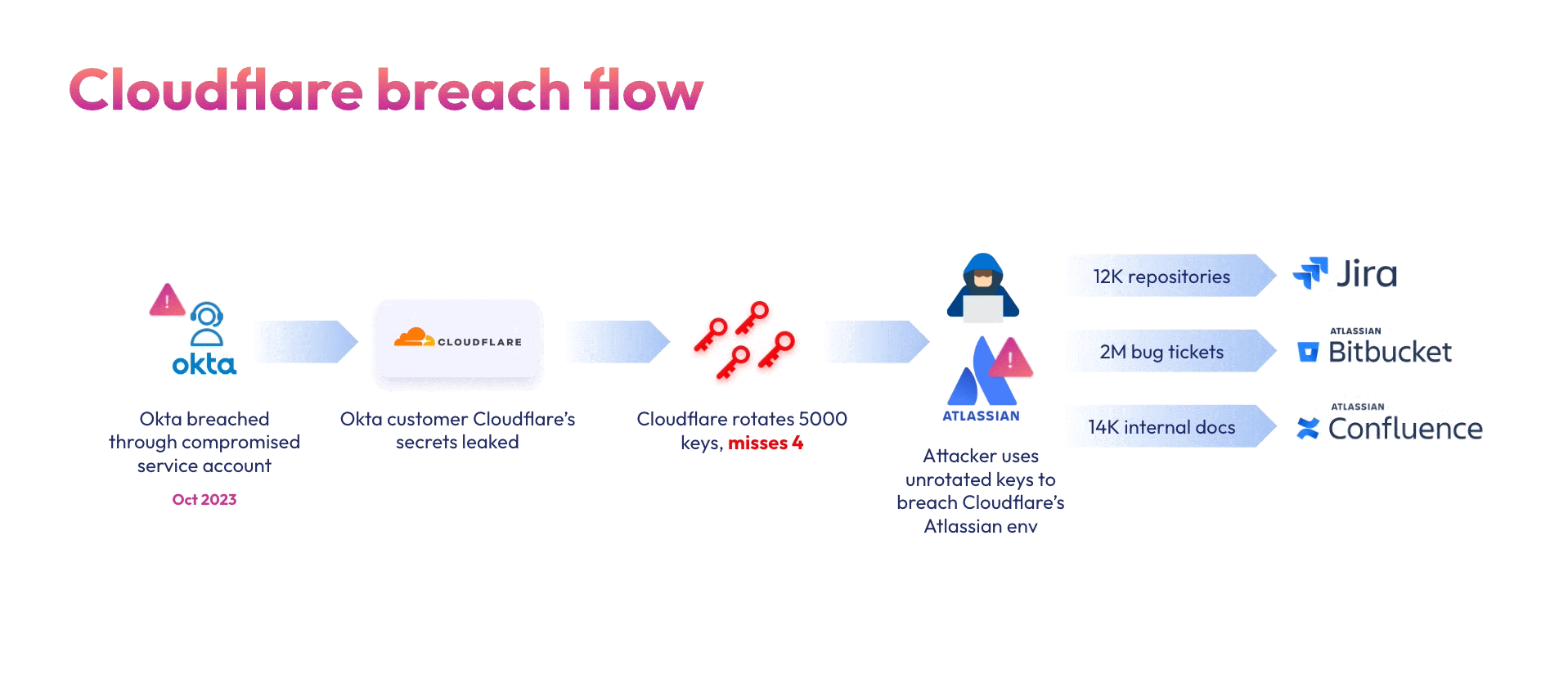
Astrix is a purposely-built solution that helps enterprises secure all non-human identities across their core systems by extending access management and threat prevention to API keys, OAuth tokens, service accounts, and webhooks.
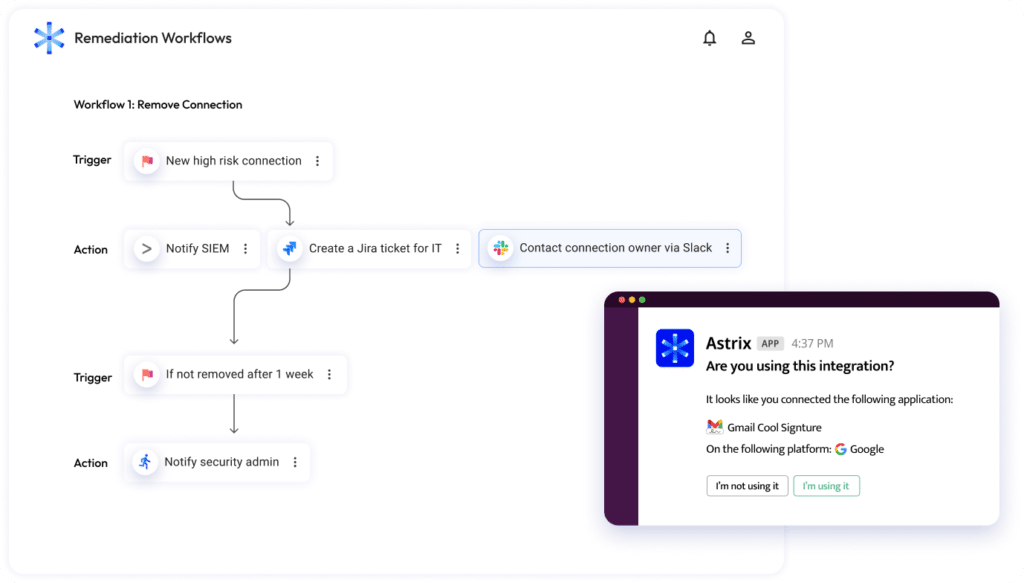
Astrix’s integration with Slack allows rapid remediation of non-human identity threats:
- Astrix Slack bot – Cut communication cycles and get user feedback faster. Whenever a user connects a third-party app into Slack, the Astrix bot sends the end user an automated message to check for business justification. Beyond fostering a better security culture, this feedback allows security teams to easily get the context they need to remediate risky access fast, and do so without worrying about breaking critical processes.
- Security events channels – Get alerted on high-risk security events that are relevant to you. For example, say Astrix detected an unusual behavior in a third-party tool connected to Microsoft Azure AD, that was flagged due to a suspicious API key accessing from abnormal geo-location. Astrix will send this information alongside the necessary security context to the relevant work group that is in charge of securing Microsoft Azure AD.
With Astrix, security teams can become enablers of GenAI adoption, automation and connectivity, while controlling the non-human identity attack surface.
Install the Astrix app for Slack: https://pages.astrix.security/secure-non-human-access-to-your-slack-environment-with-astrix-0