Non-human Access: IAM Program’s biggest blindspot
Service accounts, API keys, OAuth tokens, and other non-human identities are powerful credentials that should be protected as vigorously as user passwords.
Astrix helps you extend IAM programs to non-human identities from discovery and risk prioritization to threat detection and response.
Attackers abuse non-human identities to bypass existing security controls
Leaking an API key can be more consequential than leaking a username and password login since logins are often protected by two-factor authentication nowadays, whereas API keys are not. Recent attacks reveal attackers use access keys, service accounts, and secrets as a backdoor into companies’ most sensitive core systems and data.
Okta
Oct 2023:
Attackers used a leaked service account to access Okta’s support case management system and view files uploaded by Okta customers. Among the affected customers are CloudFlare and BeyondTruts.
Microsoft Azure AD
Jul 2023:
A stolen inactive signing key from a breached Azure system was used to create valid email access tokens, and allowed hackers to access Office365 environments across multiple organizations within the shared Azure AD cloud environment.
Jumpcloud
Jul 2023:
During an ongoing breach investigation, Jumpcloud invalidated all API keys and later urged its customers to rotate all tokens provided.

“Astrix strengthens our identity security program by providing us with continuous visibility and governance over thousands of non-human identities across the entire organization, from the corporate to the production environments.”
The vast scope of non-human access
According to Astrix Research

A company with 1,000 employees has roughly 10,000 tokens granting different applications access to its core system.

12% of apps connected to Google Workspace are considered to be published by untrustworthy vendors.

30% of access tokens detected in Salesforce are no longer in use and can be safely removed without impacting the business.
Existing IAM solutions don’t cut it

Ungoverned machine credentials
Tools like CASB, MFA, SSO and password managers protect usernames and password logins. We help you monitor and secure programmable access credentials like API keys, OAuth tokens, service accounts and SSH keys.

Limited Threat Detection & Response
Existing Identity Threat Detection and Response (ITDR) tools specifically monitor user identity systems and user activity logs for attacks. Astrix helps extend ITDR to non-human identities and monitor them for misuse and compromise.

Secure user access only
Identity Governance and administration (IGA) solutions manage only user identities and secure user access. Astrix provides the visibility and context required to secure non-human identity, access, and activity.

Context-less secrets protection
Vaults only store your secrets without any security or business context. Secret scanners only find exposed secrets without risk prioritization. Astrix helps you understand where your exposed secrets are, if they’re valid, if they’re being used and what permissions they have – so you can prioritize risk and prevent threats.
How Astrix helps identity teams control non-human access
Continuous discovery and inventory of all non-human identities and access permissions
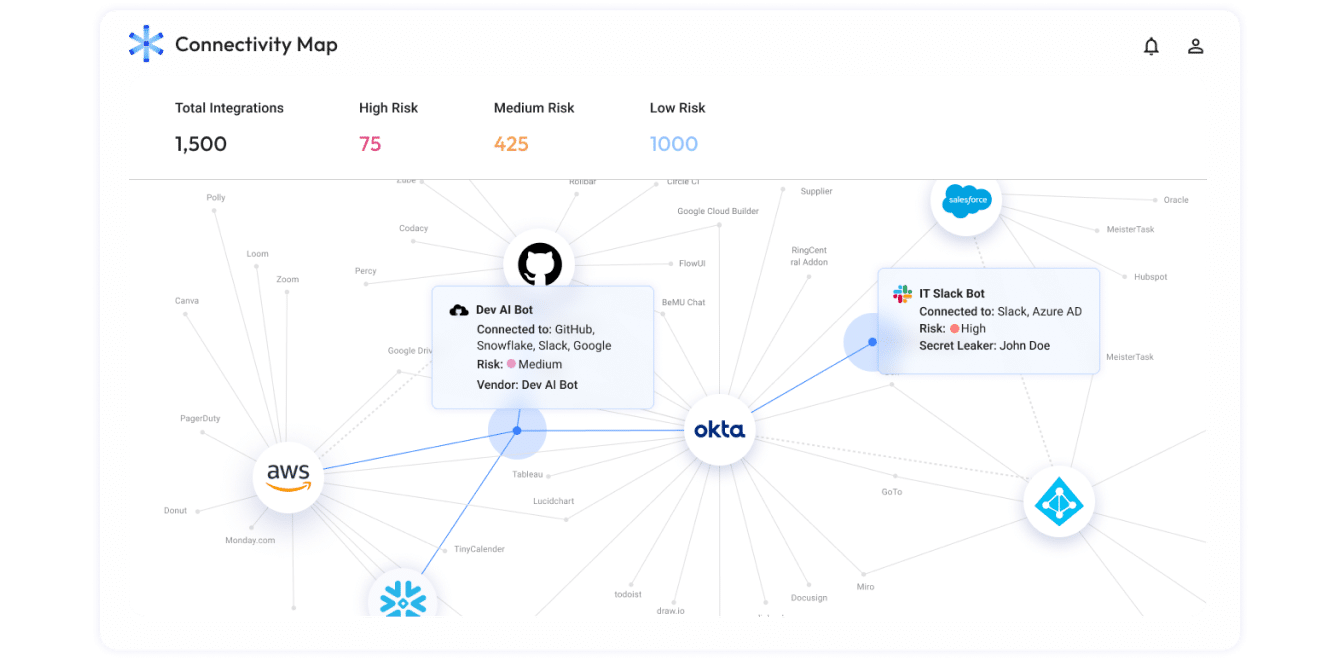
Get a straightforward, consolidated view of:
- Third-party apps and Gen AI services connected to core business and identity systems.
- Shadow access to the engineering environment (for example, an API key issued by a developer to test a new CI/CD service).
- Issued OAuth tokens, API keys, service accounts, SSH keys, and webhooks.
- Permissions granted and data exposures.
- Connection users and usage levels.
- Indirect connections via no-code/low-code automation platforms.
- Vendor supply-chain list.
Instantly improve identity security hygiene with risk prioritization and context
Get a prioritized list of security alerts with all the business context you need to remediate over-privileged, unnecessary, and untrusted non-human access. So you can make smarter decisions without breaking anything.
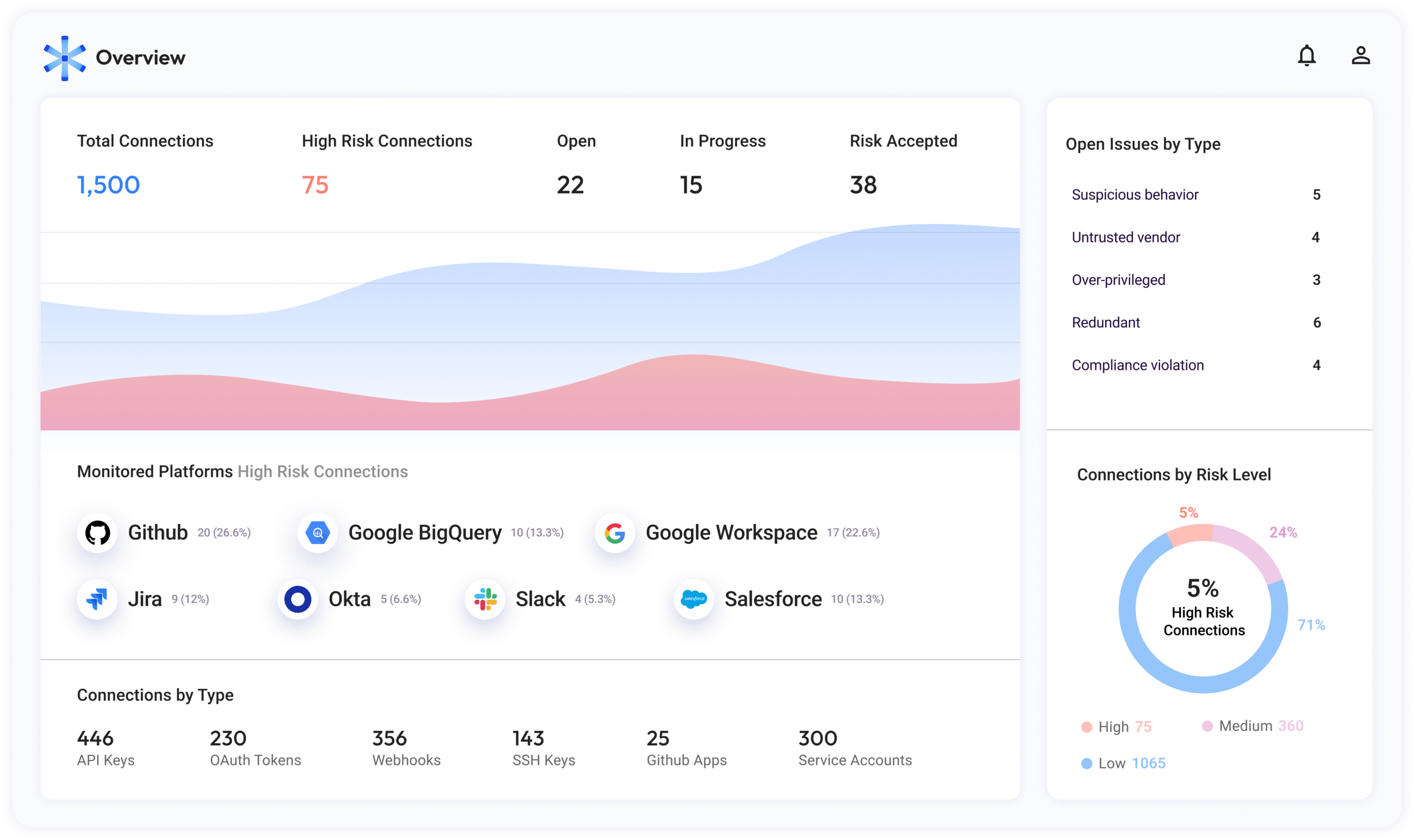
- Misconfigured and over-privileged access.
- The business context of each connection, access token, and service account.
- Redundant apps, tokens, and keys of past employees and invalid applications.
- Dangerous practices, such as granting the same access keys to multiple services.
Detect & remediate suspicious non-human access in real-time through behavior analysis
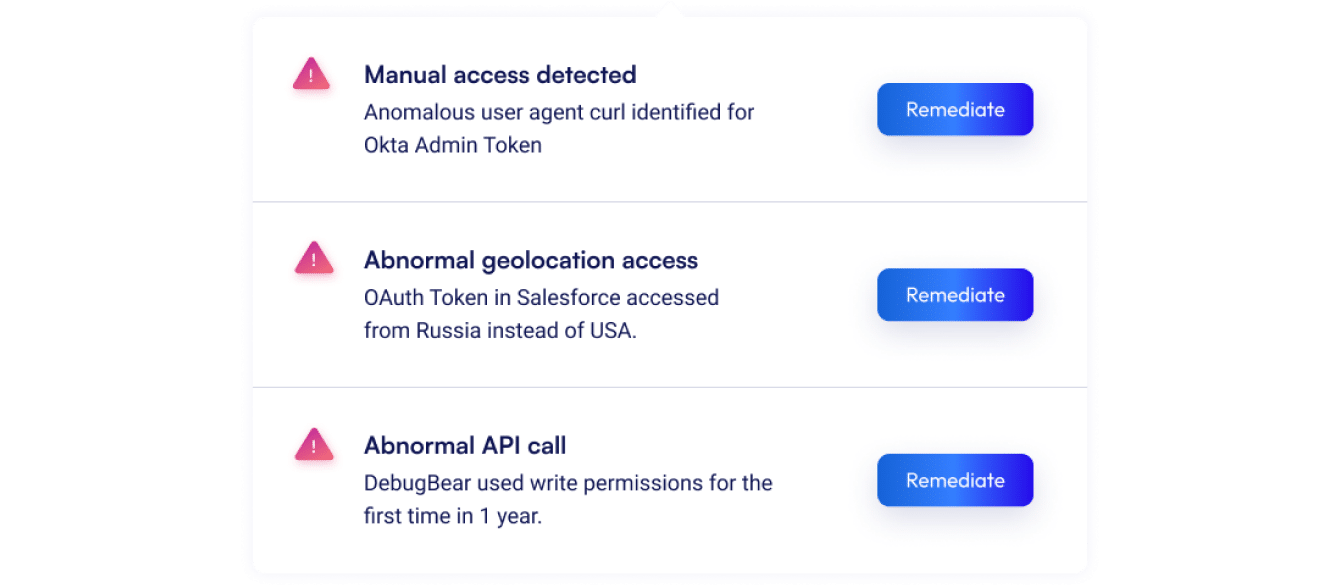
- Access from suspicious geo-locations.
- A service or secret that uses out-of-the-ordinary permissions.
- Unusual user agent.
- Anomalous ISP.
Keep track of every access token, from creation to expiration
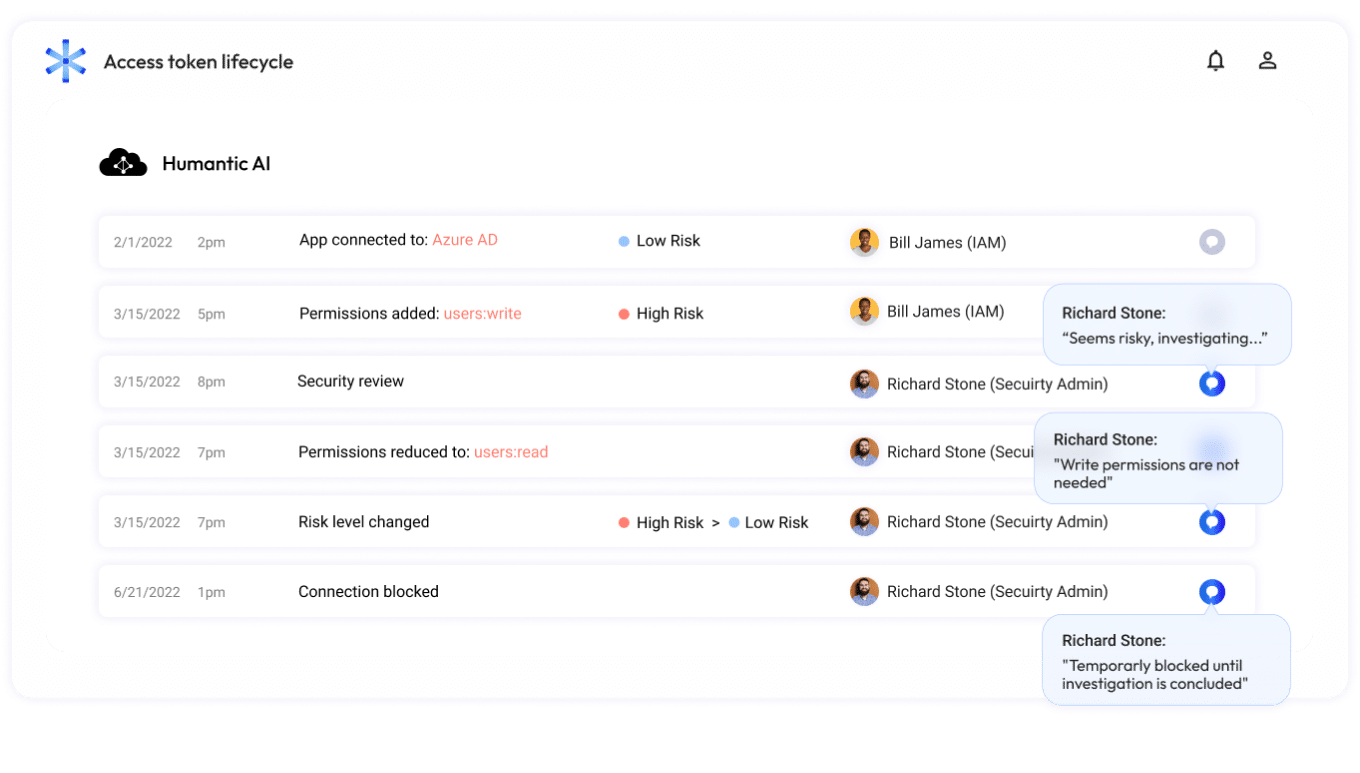
Understand your non-human access risks at every stage:
- See the issues related to suspicious connections’ behavior, escalated permissions, and ownership changes.
- Monitor risk changes to identify connections that were potentially impacted by a vulnerability such as Log4j.
- Detect repeatable connection issues to enhance your threat response.
Continuous discovery and inventory of all non-human identities and access permissions

Get a straightforward, consolidated view of:
- Third-party apps and Gen AI services connected to core business and identity systems.
- Shadow access to the engineering environment (for example, an API key issued by a developer to test a new CI/CD service).
- Issued OAuth tokens, API keys, service accounts, SSH keys, and webhooks.
- Permissions granted and data exposures.
- Connection users and usage levels.
- Indirect connections via no-code/low-code automation platforms.
- Vendor supply-chain list.
Instantly improve identity security hygiene with risk prioritization and context
Get a prioritized list of security alerts with all the business context you need to remediate over-privileged, unnecessary, and untrusted non-human access. So you can make smarter decisions without breaking anything.

- Misconfigured and over-privileged access.
- The business context of each connection, access token, and service account.
- Redundant apps, tokens, and keys of past employees and invalid applications.
- Dangerous practices, such as granting the same access keys to multiple services.
Detect & remediate suspicious non-human access in real-time through behavior analysis

- Access from suspicious geo-locations.
- A service or secret that uses out-of-the-ordinary permissions.
- Unusual user agent.
- Anomalous ISP.
Keep track of every access token, from creation to expiration

Understand your non-human access risks at every stage:
- See the issues related to suspicious connections’ behavior, escalated permissions, and ownership changes.
- Monitor risk changes to identify connections that were potentially impacted by a vulnerability such as Log4j.
- Detect repeatable connection issues to enhance your threat response.
Non-human access is growing exponentially
The modern enterprise is a breeding ground for shadow non-human access
Gen AI, IT democratization and Bottom-up SW adoption
Businesses rely on generative AI tools and third-party apps to advance their operations and increase productivity. With nearly 200 generative AI apps created weekly and SaaS vendors like Okta, Google Workspace, Salesforce, and Microsoft 365 offering thousands of integrations in their marketplace alone, ‘non-technical’ employees are empowered to create third-party connections into these core systems. However, due to a lack of cybersecurity awareness, they may unknowingly connect untrusted, over-privileged, and later unused third-party apps to their accounts.
The “engineering” black hole of tokens
IT teams, DevOps, and others increasingly provide API-based access to third-party applications and Gen AI services from core systems like GitHub or Snowflake. These shadow integrations (created using API keys, service accounts, webhooks, OAuth tokens, or even SSH keys) create another whole ecosystem of supply chain dependencies. In addition, growing connectivity between internal services and resources to core engineering systems leads to many secrets scattered across SaaS, IaaS, machines, and workstations. While Dev teams create these secrets, security teams lack the visibility and the context to secure them.







