Secure and manage non-human identities
Discover and remediate over-privileged and suspicious API keys, OAuth apps and service accounts that expose you to supply chain attacks and data breaches.
















We secure NHIs across SaaS, IaaS and PaaS environments
From Salesforce and Office 365 to GitHub,
AWS, Azure and BigQuery, we ensure your
environments are protected from NHI risks.
Agentless
We are a non-proxy
API-based solution.
Easy to deploy
Connect us to your core system in minutes with a few clicks.
Non-intrusive
We respect your privacy by reading your metadata only and asking for minimal permissions.
Control non-human identities
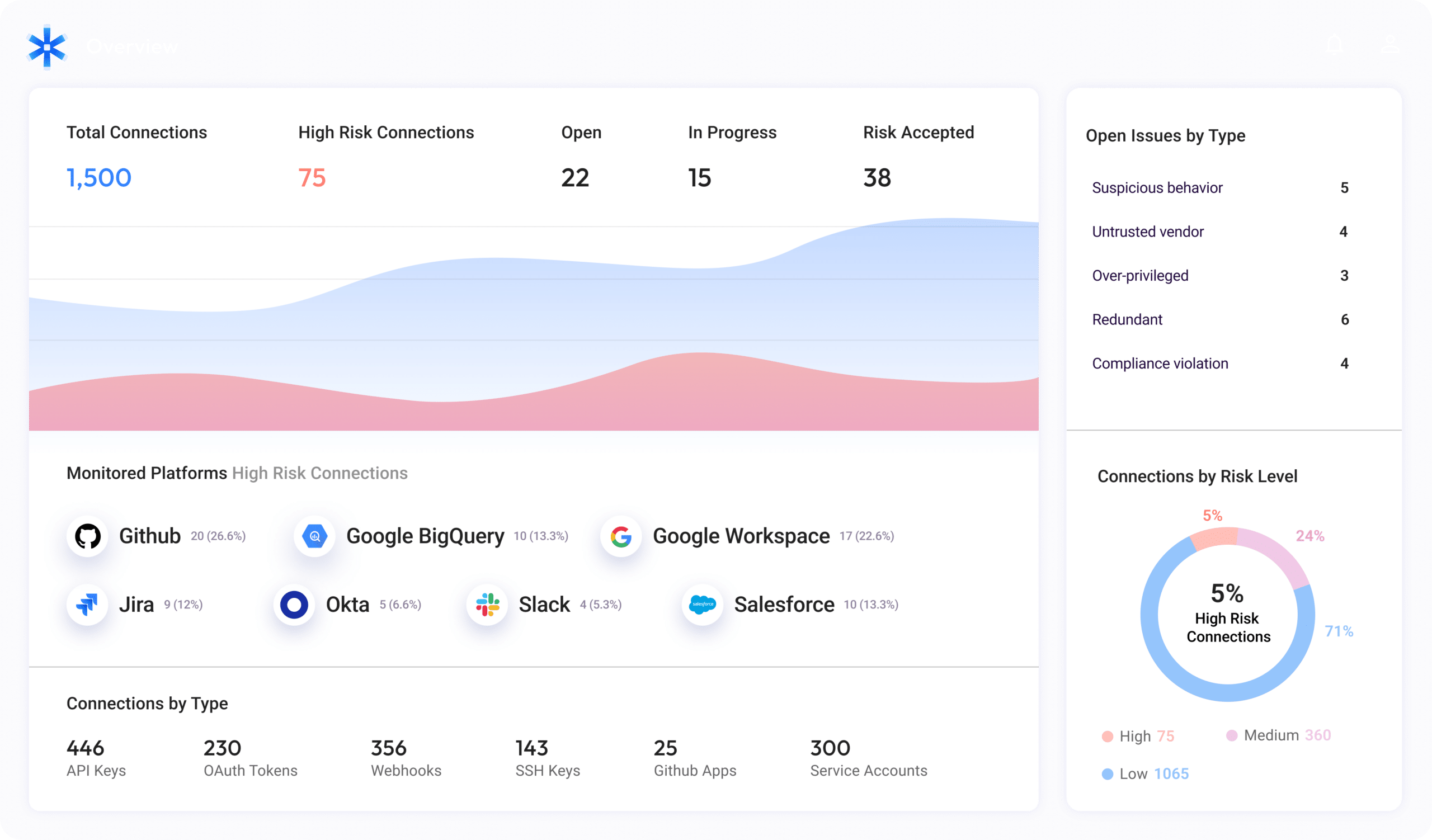
Real-time discovery & mapping of NHIs
Get a complete and up-to-date inventory of all non-human identities accessing your environments – from GitHub, Salesforce and Microsoft365 to AWS, GCP, Okta and Snowflake:
Get a straightforward, consolidated view of:
- Third-party app access
- Shadow identities (for example, an API key issued by a developer to test a new CI/CD service)
- Issued OAuth tokens, API keys, service accounts, SSH keys, and webhooks
- Indirect connections via no-code/low-code automation platforms
- Vendor supply-chain list
NHI risk prioritization with rich context
Reduce your NHI attack surface without breaking critical processes. Get the risk and business context you need to remediate over-privileged, redundant and untrusted NHI access.
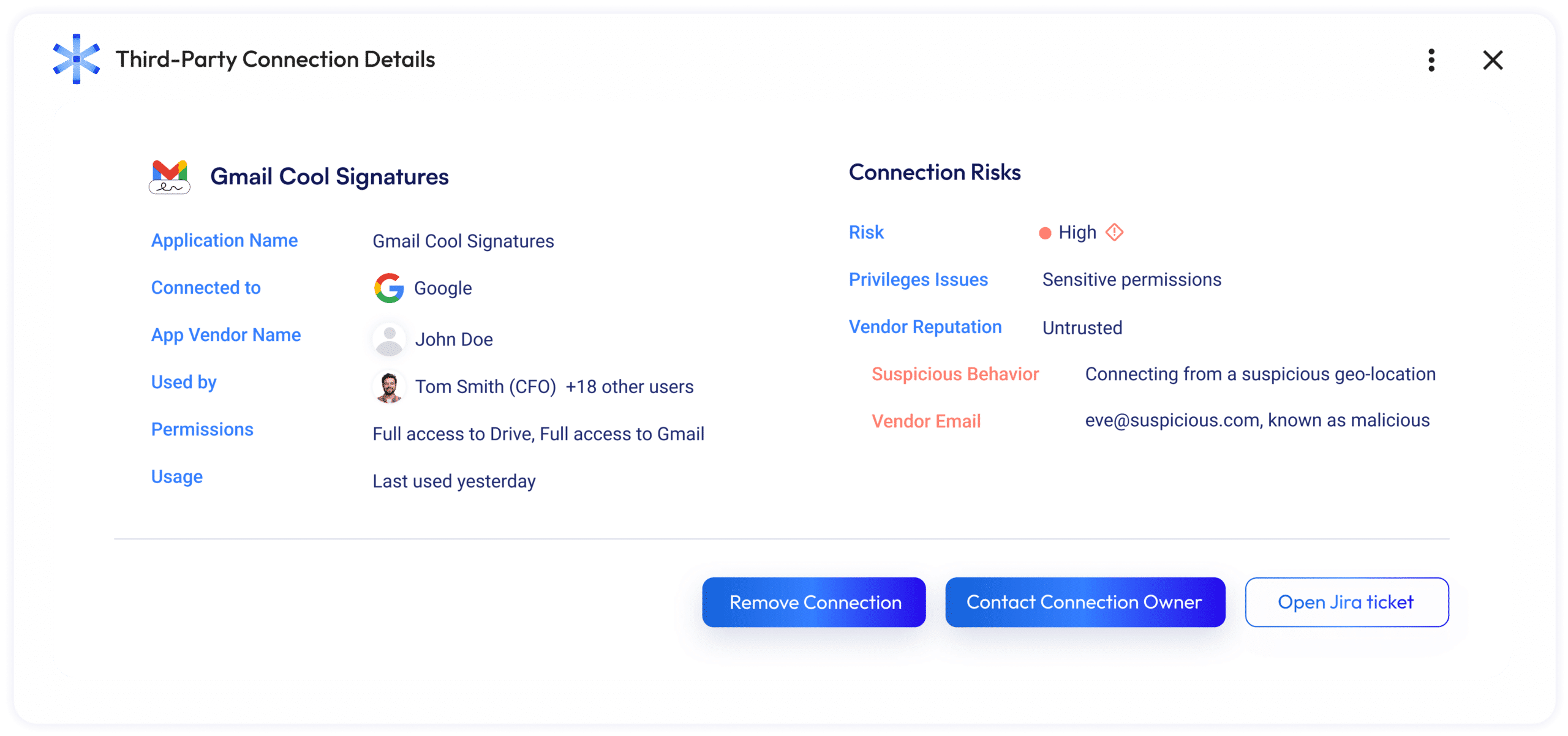
- Misconfigured and over-permissive identities
- Malicious third-party access such as impersonating apps and OAuth phishing attacks
- Redundant apps, tokens, and keys of past employees and invalid applications
- The business context of each OAuth app, API key and service account, so you can make smarter decisions without breaking anything
- Dangerous practices, such as granting the same access keys to multiple services
Detect NHI abuse in real-time
Leverage real-time behavior analysis to detect and respond to anomalous NHI activity that indicates a possible threat.

Our anomaly detection engines continuously analyze identities, services and vendors and how they connect to and within your organization, to detect attacks before they happen:
- Access from a suspicious geo
- A service that is using out of the ordinary permissions
- Unusual user agent
Quickly remediate with automated workflows
Use out-of-the-box policies & automated remediation workflows integrated to your security stack, and enable end-users to resolve security issues in the process.
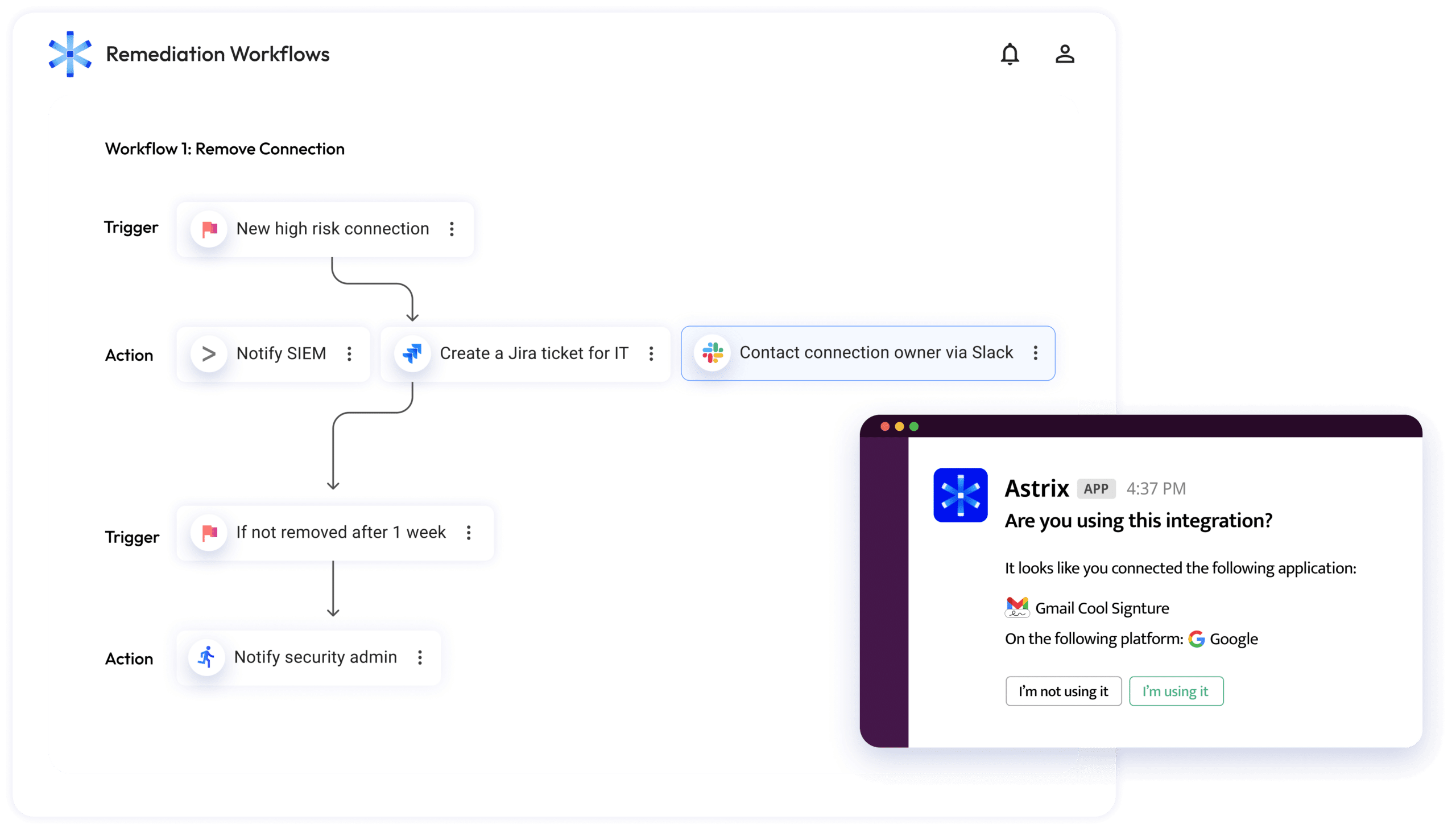
Mitigate NHI risks while keeping your team productive
- Out of the box policies allow you to instantly remediate risks and prevent attacks
- Work with your existing tech stack – get a Slack notification, automatically open a Jira ticket or work with your SIEM platform.
- Receive highly digested and prioritized security alerts including user feedback, threat context, severity level, and suggested remediation steps.
- Raise end-user awareness to the permissions they grant NHIs and foster a healthier security culture.
Manage the lifecycle of every NHI, from creation to expiry
Astrix continuously monitors every NHI from the moment it connects to your environment, and adjusts security controls when significant changes occur.
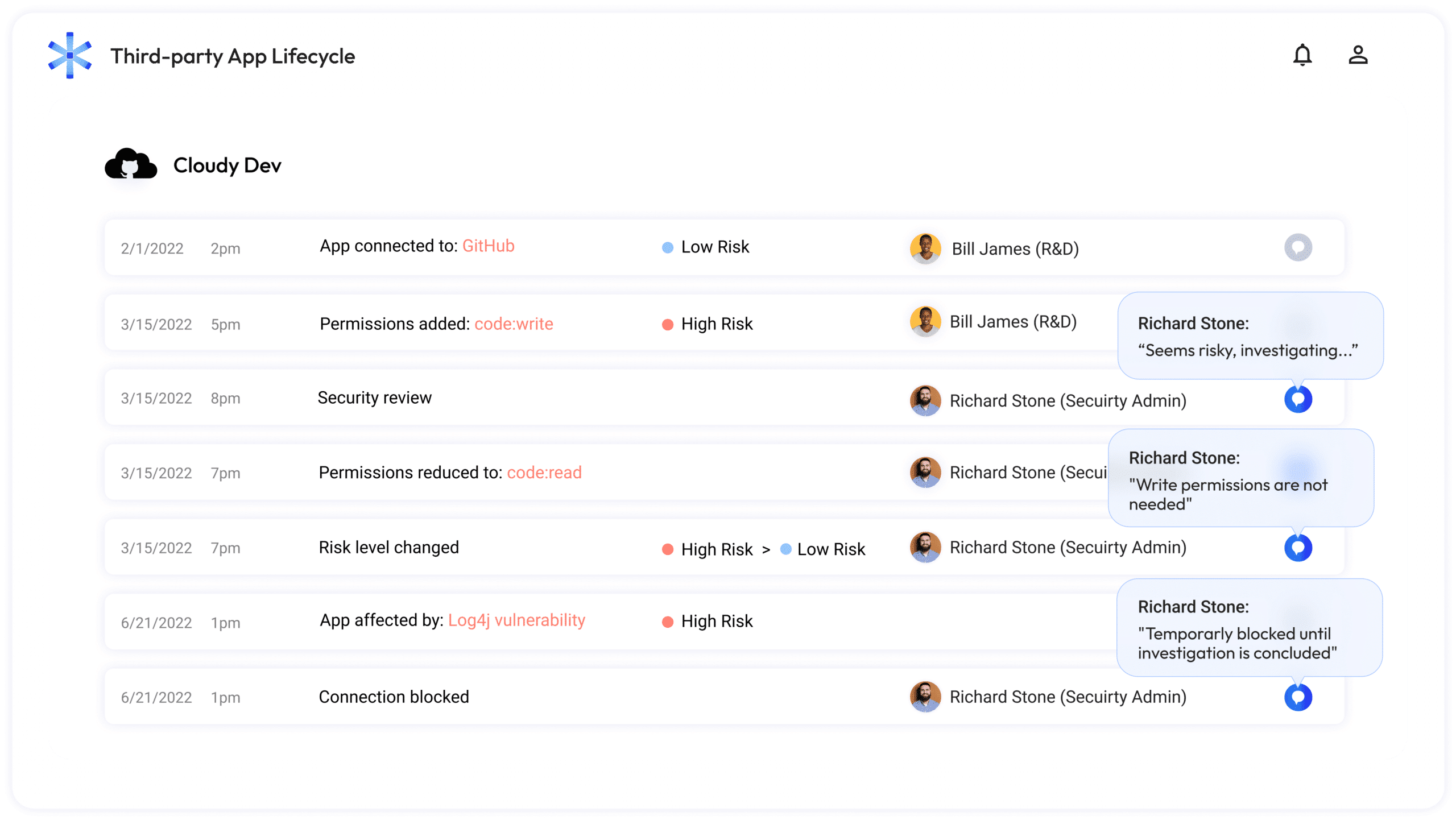
Understand your NHI risks at every stage:
- See the issues related to suspicious NHI’s behavior, escalated permissions and ownership changes
- Monitor risk changes to identify NHIs that were potentially impacted by a vulnerability such as Log4j
- Detect repeatable NHI issues to enhance your threat response
Real-time discovery & mapping of NHIs
Get a complete and up-to-date inventory of all non-human identities accessing your environments – from GitHub, Salesforce and Microsoft365 to AWS, GCP, Okta and Snowflake:
Get a straightforward, consolidated view of:
- Third-party app access
- Shadow identities (for example, an API key issued by a developer to test a new CI/CD service)
- Issued OAuth tokens, API keys, service accounts, SSH keys, and webhooks
- Indirect connections via no-code/low-code automation platforms
- Vendor supply-chain list
NHI risk prioritization with rich context
Reduce your NHI attack surface without breaking critical processes. Get the risk and business context you need to remediate over-privileged, redundant and untrusted NHI access.

- Misconfigured and over-permissive identities
- Malicious third-party access such as impersonating apps and OAuth phishing attacks
- Redundant apps, tokens, and keys of past employees and invalid applications
- The business context of each OAuth app, API key and service account, so you can make smarter decisions without breaking anything
- Dangerous practices, such as granting the same access keys to multiple services
Detect NHI abuse in real-time
Leverage real-time behavior analysis to detect and respond to anomalous NHI activity that indicates a possible threat.

Our anomaly detection engines continuously analyze identities, services and vendors and how they connect to and within your organization, to detect attacks before they happen:
- Access from a suspicious geo
- A service that is using out of the ordinary permissions
- Unusual user agent
Quickly remediate with automated workflows
Use out-of-the-box policies & automated remediation workflows integrated to your security stack, and enable end-users to resolve security issues in the process.

Mitigate NHI risks while keeping your team productive
- Out of the box policies allow you to instantly remediate risks and prevent attacks
- Work with your existing tech stack – get a Slack notification, automatically open a Jira ticket or work with your SIEM platform.
- Receive highly digested and prioritized security alerts including user feedback, threat context, severity level, and suggested remediation steps.
- Raise end-user awareness to the permissions they grant NHIs and foster a healthier security culture.
Manage the lifecycle of every NHI, from creation to expiry
Astrix continuously monitors every NHI from the moment it connects to your environment, and adjusts security controls when significant changes occur.

Understand your NHI risks at every stage:
- See the issues related to suspicious NHI’s behavior, escalated permissions and ownership changes
- Monitor risk changes to identify NHIs that were potentially impacted by a vulnerability such as Log4j
- Detect repeatable NHI issues to enhance your threat response
Trusted by industry leaders










Astrix meets the highest industry standards





Blog & News
Blog
News

OAuth attack against Microsoft by Midnight Blizzard

Astrix Security named a Cool Vendor in the 2023 Gartner Cool Vendors in Identity-First Security

GhostToken – Exploiting GCP application infrastructure to create invisible, unremovable trojan app on Google accounts

13 non-human identity attacks in 16 months

Slack’s GitHub breach: 6 tips to avoid similar attacks

Insecure third-party connections to your GitHub may trigger a supply chain attack

CircleCI Security Alert – Are You at Risk?

The promise and peril of third-party integrations

PLG and security leaders: going with the flow

How to Close the Service Account Security Gap in GCP and Snowflake

Astrix Security Named Winner of Global InfoSec Award at RSA 2022
VentureBeat – Third-party app attacks: Lessons for the next cybersecurity frontier

GitHub Apps Bug Created Significant 3rd-Party Risk: How You Can Stay Protected

2022 Recap: 6 Surprising Third-Party Connectivity Stats

5 cloud-app connectivity trends for 2022

OAuth attack against Microsoft by Midnight Blizzard

Astrix Security named a Cool Vendor in the 2023 Gartner Cool Vendors in Identity-First Security

Astrix Security Raises $25M in Series A Funding

Astrix Security Named a Finalist for RSA Conference 2023 Innovation Sandbox

Astrix Security Takes Home Three Coveted Global InfoSec Awards

Astrix Security Named a Finalist for RSA Conference 2023 Innovation Sandbox
Security Boulevard – Supply Chain Dependency: What Your GitHub Connections May Trigger

Dark Reading – The Next Generation of Supply Chain Attacks is Here to Stay

20 Minute Leaders: Leadership & the Future of App-to-App Security
DrZeroTrust: Securing App-to-App Connectivity and Low or No Code Apps

DevOps Paradox: Security Concerns in Low-Code and No-Code Applications

[New eBook] The Ultimate Guide to Securing App-to-App Integrations
Securing everything connected. Not just everyone.



