
Secure non-human access to engineering environments
A new type of supply chain attacks is taking advantage of machine identities, access keys and tokens connecting internal and third-party cloud services to engineering environments. Astrix helps AppSec teams secure all access keys and tokens, both internal and external.
The overlooked cause of software supply chain attacks
Existing AppSec solutions are focused on securing code and DevOps pipelines. However, attackers are increasingly penetrating engineering ecosystems through ungoverned programmable access – non-human connections done through secrets, service accounts, and tokens.
Slack
Threat actors gained access to Slack’s externally hosted GitHub repositories via a “limited” number of stolen Slack employee tokens.
Circleci
Following a breach, CircleCI urge their customers to rotate all secrets, and API keys.
GitHub
Repos from deprecated GitHub organizations were cloned by a compromised Personal Access Token (PAT) and then used to access sensitive information.

“Astrix helps us to deal with a growing challenge – tracking the lifecycle and the behavior of a token, especially when provided to a third-party. Astrix creates unprecedented visibility and changes the game for us”
The vast scope of ungoverned non-human access
According to Astrix Research

Dev teams create around 20-30 new personal access tokens and SSH keys in GitHub organizations every week

In a typical GitHub environment approximately 1 of 4 tokens (PAT and SSH keys) is not in use and can be safely removed without impacting the business

1 in 5 users in a Snowflake production environment is in fact a service account
Vaults, IAM or AppSec solutions won’t do

Secret managers (Vaults)
Vaults tell you what happens inside your vault, we also tell you what happens outside them: Have all your secrets been properly stored in the vaults? Were secrets copied before they were stored? Was a secret leaked?

Secret scanners
Secret scanners only detect secrets, without any context. We help you understand whether the secrets are valid, if they’re being used and what permissions they have – so you can prioritize risk and quickly improve your posture.

CNAPP solutions
While these tools secure misconfigurations inside your IaaS environments, we give you visibility and context for known or unknown connections with external cloud services.

IAM solutions
Tools like CASB, MFA and SSO only secure user access. We help you secure non-human identities and access tokens.
How Astrix helps AppSec
leaders keep their app safe
See, contextualize and safeguard your secrets from creation to expiry
- See exposed secrets across vaults and cloud environments.
- Get the context you need about exposed secrets permissions, owner, leaker and related service connections.
- Get alerted on anomalous behavior that indicates a secret has been exploited.
- Get prioritized remediation guidance for exposed secrets that put you at risk.
Get the risk and business context you need to easily remediate over-privileged, unnecessary, and untrusted access
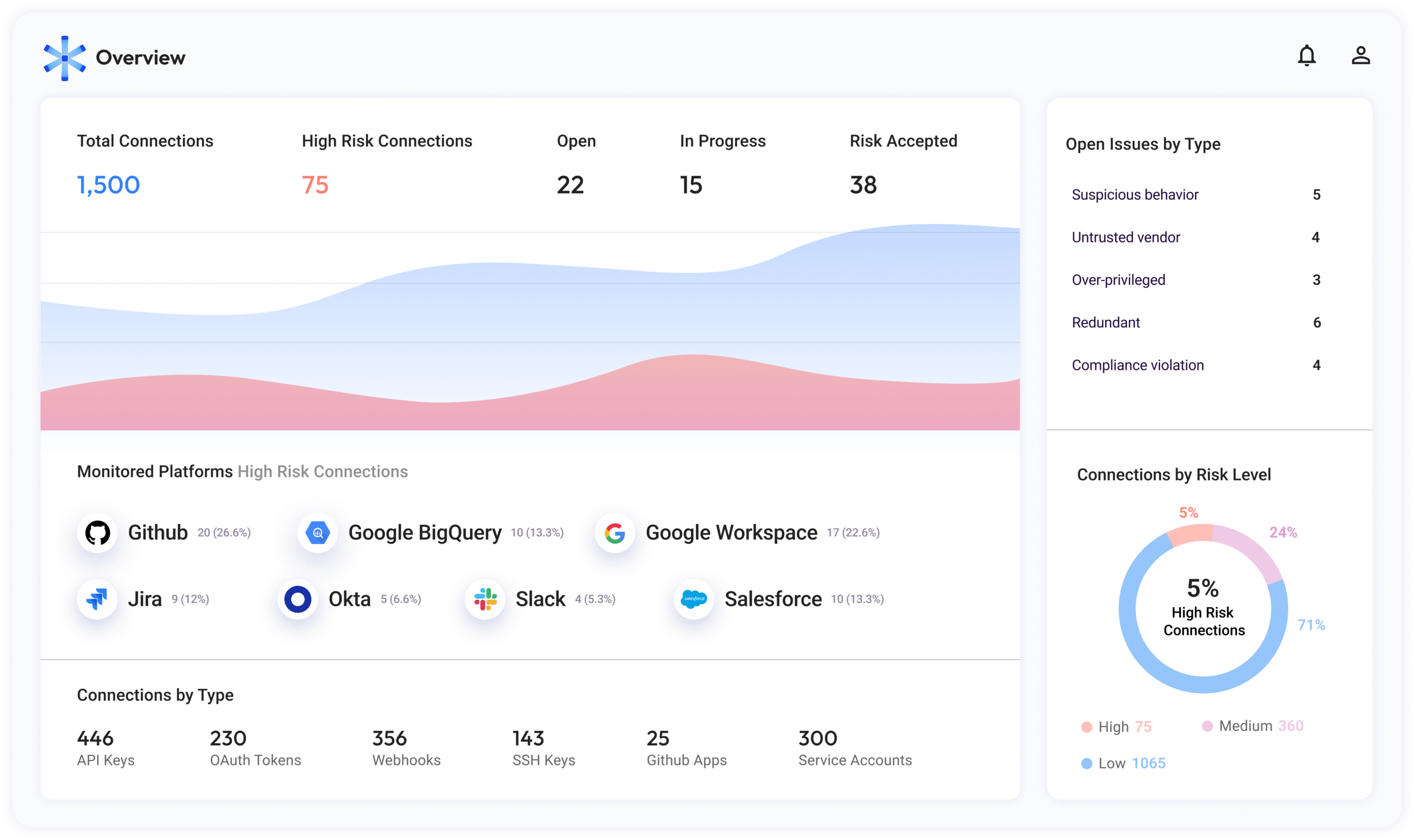
- Misconfigured and over-permissive access.
- Redundant apps, tokens, and keys of past employees and invalid applications.
- Malicious third-party connections.
- Dangerous practices, such as granting the same access keys to multiple services.
- The business context of each connection, key and service account, so you can make smarter decisions without breaking anything.
Detect & remediate suspicious non-human access in real-time through behavior analysis
- Access from a suspicious geo.
- A service or secret that is using out of the ordinary permissions.
- Unusual user agent.
- Anomalous ISP.
See, contextualize and safeguard your secrets from creation to expiry
- See exposed secrets across vaults and cloud environments.
- Get the context you need about exposed secrets permissions, owner, leaker and related service connections.
- Get alerted on anomalous behavior that indicates a secret has been exploited.
- Get prioritized remediation guidance for exposed secrets that put you at risk.
Get the risk and business context you need to easily remediate over-privileged, unnecessary, and untrusted access

- Misconfigured and over-permissive access.
- Redundant apps, tokens, and keys of past employees and invalid applications.
- Malicious third-party connections.
- Dangerous practices, such as granting the same access keys to multiple services.
- The business context of each connection, key and service account, so you can make smarter decisions without breaking anything.
Detect & remediate suspicious non-human access in real-time through behavior analysis
- Access from a suspicious geo.
- A service or secret that is using out of the ordinary permissions.
- Unusual user agent.
- Anomalous ISP.
Two types of non-human access in engineering environments
Internal non-human access
R&D teams regularly generate ‘secrets’ – keys and tokens which allow machine access to resources, code and infrastructure – aka your most valuable intellectual property, and the vitality of your app. These keys are scattered across different secret managers, and regularly accessed by engineers that often unintentionally expose them (for debugging, for example). Security teams lack visibility into these keys and tokens – where they are, what they allow access to, what permissions they have.
Third-party non-human access
Employees regularly connect third-party services to core engineering environments like GitHub, GitLab, AWS and BigQuery to improve productivity. These shadow non-human connections are done via API keys, service accounts, webhooks, OAuth tokens, or SSH keys, which are often created with wide permissions and unlimited, permanent access. Many of these are never revoked even after users are finished with the connected service.
Related Resources

Slack’s GitHub breach: 6 tips to avoid similar attacks

Not just code vulnerabilities: The overlooked cause of software supply chain attacks

GhostToken – Exploiting GCP application infrastructure to create invisible, unremovable trojan app on Google accounts

Sumo Logic: Compromised non-human access leads to potential supply-chain exploits



