Story 1: Removing super-admin tokens across 33 GitHub tenants in 2 hours
Join Astrix customers as they lead the non-human identity security frontier in this series “The Astrix stories: Real customer wins”. From building an automated process around NHI offboarding, to a collaboration between security and engineering to remove super-admin tokens in two hours – these real stories will help you understand what an NHI security strategy looks like for Astrix customers.
Chapter 1: Did we actually rotate all compromised keys?
Ever wondered who has access to your keys and tokens other than you? How would you know?
A leading SaaS provider asked this question after one of their trusted vendors was compromised. With over 12,000 diverse employees including a global engineering team, multiple business units, a vast salesforce, and a complex digital infrastructure across cloud and on-premises technologies, the company’s security challenges are multifaceted, and non-human identities (NHIs) such as tokens, secrets and service accounts were a total blindspot.
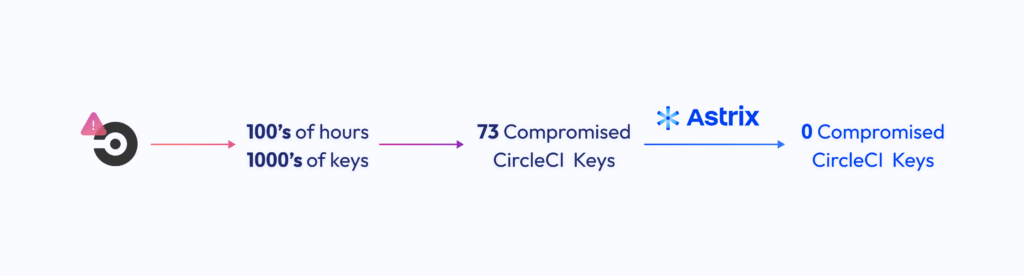
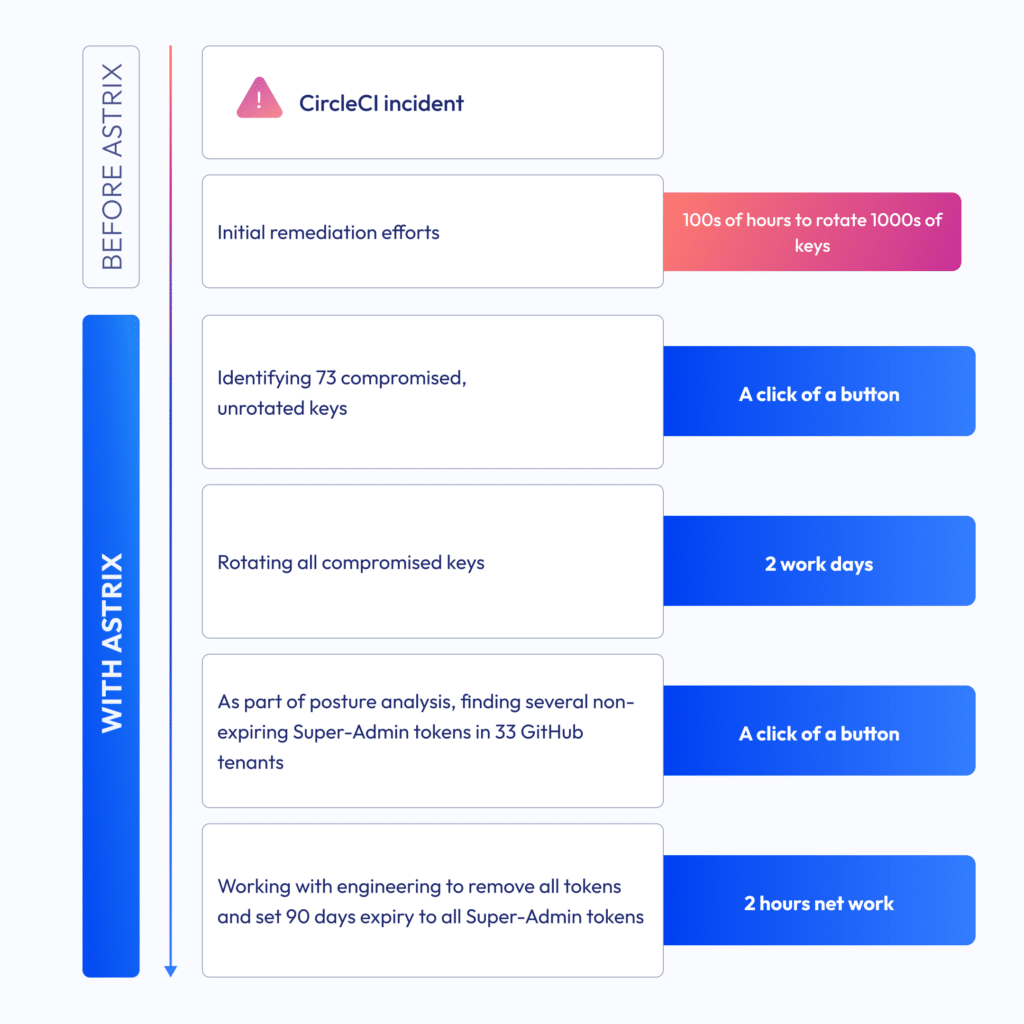
As a result of the CircleCI incident of January 2023, the security team’s main focus was to manually identify thousands of keys that covered this diverse ecosystem, their dependencies, and business impact, and then rotate every single key. This effort alone took hundreds of hours of engineering time and proved fruitful with the successful identification & rotation of the compromised keys. However, the question remains – how do we know we caught everything?
This is where Astrix Security came in. As part of the continuing CircleCI remediation effort, the security team leveraged Astrix’s capabilities to identify and remediate risky tokens, secrets, and keys across their GitHub organizations. Astrix’s inventorying capabilities were put to the test, resulting in the detection of 73 compromised CircleCI identities across 6 of 33 GitHub organizations.
Needless to say, the security team was shocked.
Using Astrix’s comprehensive security and business context, the company’s engineering team, supported by their security team, was able to rotate the compromised keys in a matter of a couple of days—a process that might have otherwise taken months or gone unnoticed until much greater damage occurred.
Chapter 2: Implementing zero-trust for NHIs
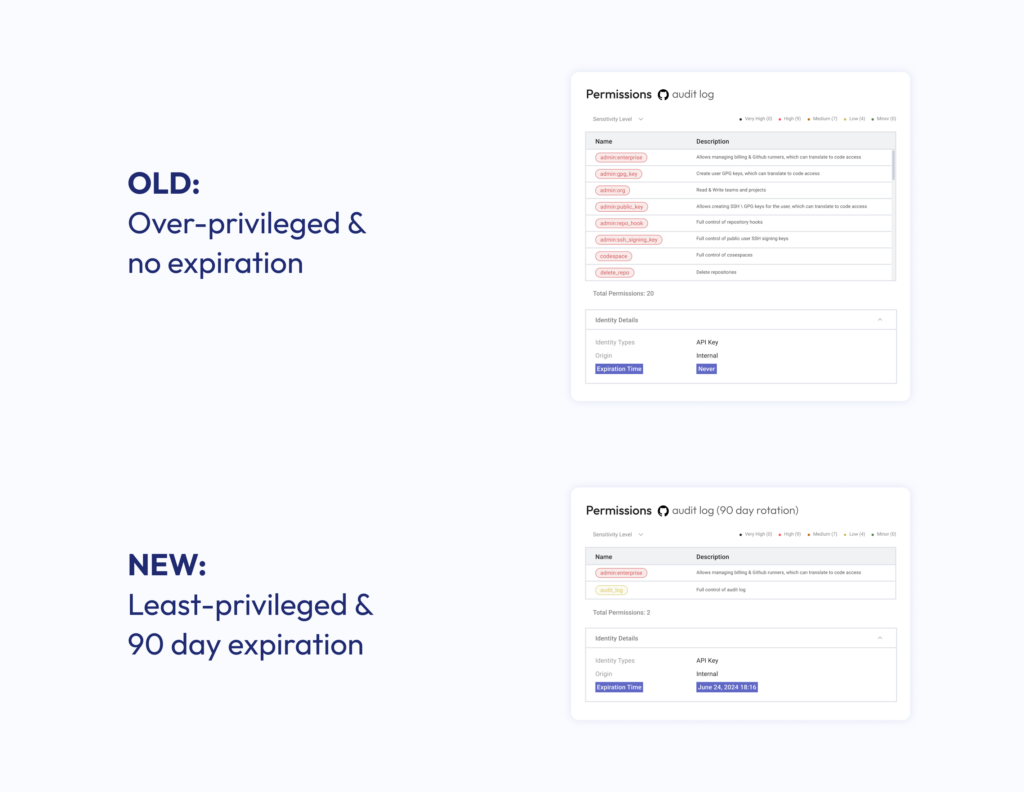
Fast-forward to March 2024. The company’s security posture has evolved dramatically due to this new focus on the non-human identity layer. Using Astrix, the security team conducted a deep dive into their environments and discovered several Super-Admin tokens with no expiration across 33 GitHub organizations.
Now completely NHI-savvy, the security team recognized the extreme risk posed by Super-Admin tokens, even without being GitHub experts. Knowing such tokens could potentially allow malicious actors to delete the company’s entire GitHub presence, they took decisive action. With the data to back them up, the team collaborated with engineering to eliminate the risk and implement best practices for tokens. Together, within a couple of hours of work, they removed the risky tokens, and introduced a policy around token rotation and least privilege with a 90-day expiration, effectively neutralizing the threat.
Chapter 3: Becoming NHI experts
This story illustrates a few important things beyond the specific “case study” of CircleCI compromise and super-admin tokens. Since they started using Astrix, the customer’s security team has gained expertise in an area that was completely unknown before. This NHI expertise not only allowed them to close crucial security gaps, but also helped them implement essential best practices company-wide, removing the friction between security and engineering or other business units, and raising security awareness for the everyday use and abuse of NHIs.
Leveraging this newly found expertise, the security team can now enforce NHI policies and best practices across different environments and business platforms, without needing platform-specific expertise. This helps them ensure tight security as well as become enablers of the automation and connectivity that NHIs allow.
Stay tuned for story 2…