Securing non-human identities in Microsoft 365 & Azure AD
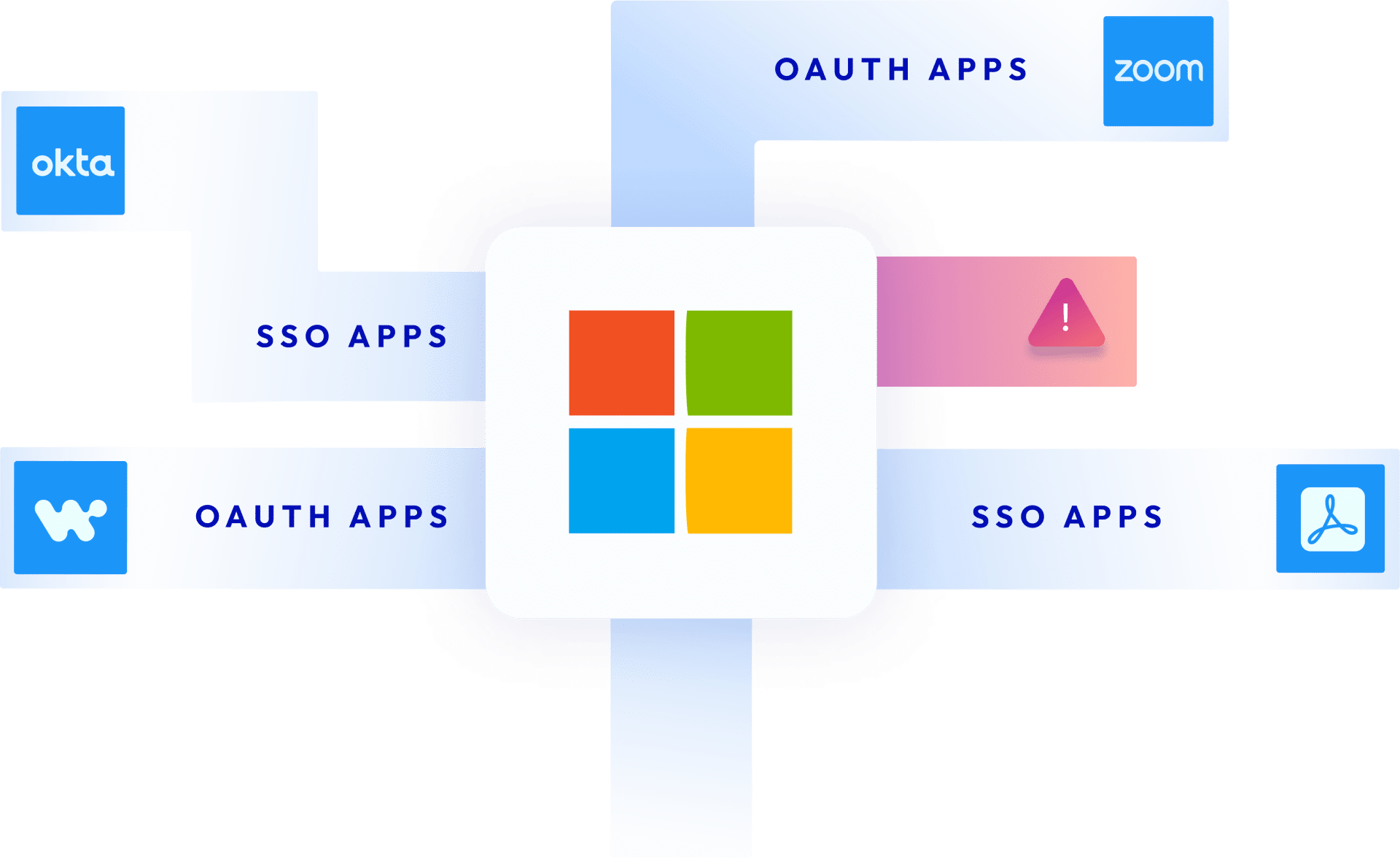
To streamline workflows and maximize its functionality, Microsoft 365 & Azure Active Directory (AAD) can be connected to thousands of apps and services, as well as a large number of non-marketplace apps that can be connected via webhooks, OAuth tokens, API keys and workflow automation platforms. Each and every connection made between Microsoft 365 and these third-party apps poses a security threat to your company, from supply chain attacks to data breaches and compliance violations.
Microsoft 365 and AAD are used by more than a million companies around the world.With the increase of decentralization of IT, API first solutions, the Saasification of code and Low Code/no code capabilities, the numbers of third party apps and services connected to these core, business sensitive platforms are only rising.
The risks of unmonitored app-to-app connections and non-human access to Microsoft 365 environments
The recent year has seen an uptick in attacks carried out via access granted to third-party cloud services, as cyber criminals exploit these connections to penetrate companies’ Microsoft 365 environments. Here are just some examples:
- Microsoft OAuth Phishing Attack (December 2022): Malicious OAuth apps were used to steal customers’ emails. The threat actors then used these accounts to register verified OAuth apps in Azure AD for consent phishing attacks targeting corporate users in the UK and Ireland.
- Microsoft OAuth (September 2022): By exploiting OAuth integrations, malicious applications were deployed on compromised cloud tenants. From there, they modified Exchange Online settings to spread spam.
- Cyber security analysts recently discovered a major vulnerability in Microsoft Teams’ desktop app. They found that the app stores user authentication tokens in clear text, without sufficiently protecting them, which gives bad actors the opportunity to steal the tokens and then infiltrate a user’s account.
- In January 2022, Office 365 customers received phishing emails that aim to trick them into giving OAuth permissions to a bogus app that then lets attackers read and write emails.
Your Microsoft 365 environment could be more exposed than you think
Using the Astrix Security platform, we discovered that organizations’ Microsoft environments are far more exposed to third-party applications than they think.
From our research we discovered Microsoft environments have:
- Hundreds of connections to third-party applications and cloud services.
- New connections seen on a weekly basis.
- The majority of connections are applications originating from non-marketplace sources which means they are not vetted.
- Some access granted between Microsoft 365 environments and other apps is no longer used.
- Connections with common cloud services were configured with complete (and unnecessary) admin permissions.
- Many of the connections were with third-party apps and services of low-reputation publishers.
How Astrix helps secure your Microsoft environment
- Get a full inventory of all non-human access and app-to-app connections to your Microsoft 365 environment. M365 has a huge variety of connection types that you can’t really see without Astrix.
- Detect anomalous behavior for each token accessing your Microsoft 365 environment. Astrix’s anomaly detection is based on a correlation of different IoCs (Indicators of Compromise) and real-time threat intelligence. In addition, Astrix engines watch for anomalous behavior for each connection of a third-party to the M365 environment.
- Get alerts only on risks that expose you to supply chain attacks, data breaches, and compliance violations, and easily remediate them through automated workflows.