Securing non-human identities in Google Workspace
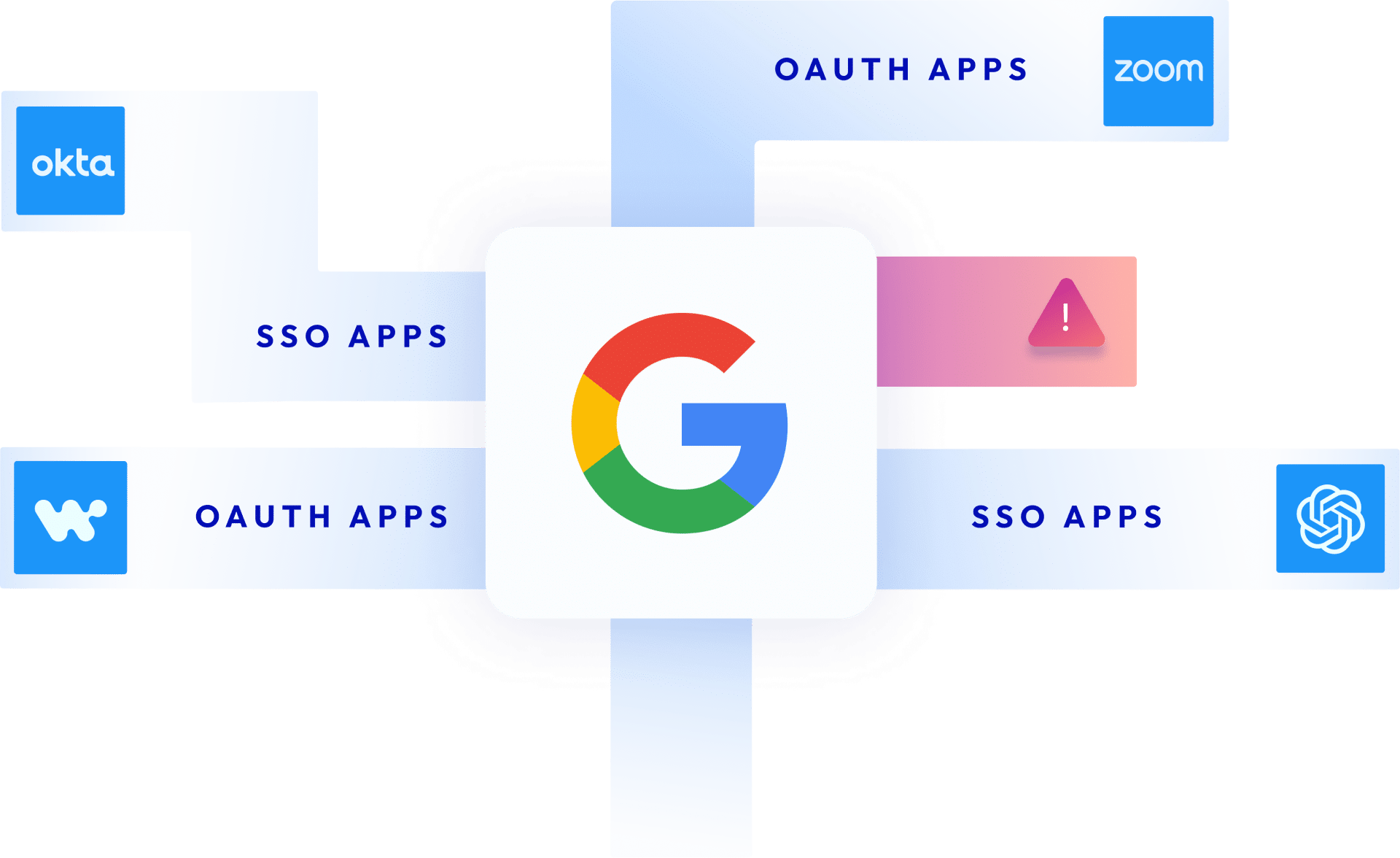
Google Workspace is a core productivity engine for many businesses. As such, employees are increasingly connecting third-party applications into their Google Email, Calendar, Docs, Drive and more in a bid to increase productivity. These connections are also created when users sign in to third-party apps using the Google Single Sign-On feature. Many of these third-party apps and add-ons (connected via OAuth tokens and service accounts) are not vetted by security teams and are often published by untrusted vendors, are over-privileged, or were connected by users who have since left the company.
While Google Workspace itself is innately secure, the more than 5,000 third-party integrations offered on the Google Marketplace and the vast ecosystem of non-public apps may not be.
The risks of app-to-app connections and unmonitored non-human access to Google Workspace environments
This unmonitored non-human access to your Google Account creates a new ecosystem of supply chain dependencies that expand your attack surface and expose your company to supply chain attacks, compliance violations, and unauthorized access. Because of the way Google Workspace and GCP connect to each other, these risks may also apply to your company’s Google Cloud Platform (GCP) environment which includes business critical platforms like BigQuery and Looker.
In environments like Google Workspace and Microsoft 365, attackers are not just using stolen OAuth tokens to penetrate organizations, but launching sophisticated ‘consent phishing’ campaigns to trick users into granting access to malicious third-party apps:
- In the 0-day vulnerability recently exposed by Astrix Security, dubbed “GhostToken”, threat actors are able to potentially change a malicious application to be invisible and unremovable, effectively leaving the victim’s Google account infected with a trojan app forever.
- In an OAuth phishing campaign, attackers used a fake service called “Google Apps” to trick users into granting them access to their email account, contacts and other online documents. The attack ultimately resulted in tens of thousands of dollars in losses for the state of Minnesota. Russian hackers (Fancy Bear) used a similar method to carry out their own set attacks with a fake malicious app called Google Defender.
- Attackers used OAuth flaws in Google and Microsoft 365’s Single Sign-On service to trick users into granting access to malicious third-party applications. The flaw allowed them to bypass phishing detection and email security solutions.
Your Google Workspace environment could be more exposed than you think
Using the Astrix Security platform, we discovered that Google environments are far more exposed to third-party apps and services than one might think.
From our research we discovered that organizations’ Google environments have:
- Thousands of access tokens connecting third-party applications and add-ons to the Google Workspace environment.
- On average, for every 5000 employees, there are 4-5 new integrations added every week.
- Risky apps that were granted excessive permissions such as the ability to see, edit, create and even delete information contained in the drive, even though the apps did not require such permissions to perform their functionality.
- Connections with apps published by untrusted vendors or individual vendors (as opposed to companies) that have a poor security reputation
How Astrix helps secure your Google Workspace environment
- Get a full inventory of all non-human access to your Google Workspace environment, and understand the risks associated with them.
- See all domain-installed applications (apps that are installed across your entire organization) to ensure they are not risky or over-permissive, and control your risk exposure.
- Get visibility and threat detection into third party services that access specific Google Workspace services such as Drive, Gmail etc – to better remediate them.
- Identify cases of over-permissive, sensitive and redundant access of third-party OAuth apps.
- Detect anomalous activity for each token accessing your Google Workspace and remediate risks – Astrix’s behavioral analysis looks into the app’s access parameters such as geolocation, IP and user agent as well as advanced behavioral parameters such unusual usage, to detect misbehaving services and apps.
- Get alerts only on risks that expose you to supply chain attacks, data breaches, and compliance violations, and easily remediate them through automated workflows.