DISCOVERY
Discover Non-Human Identities
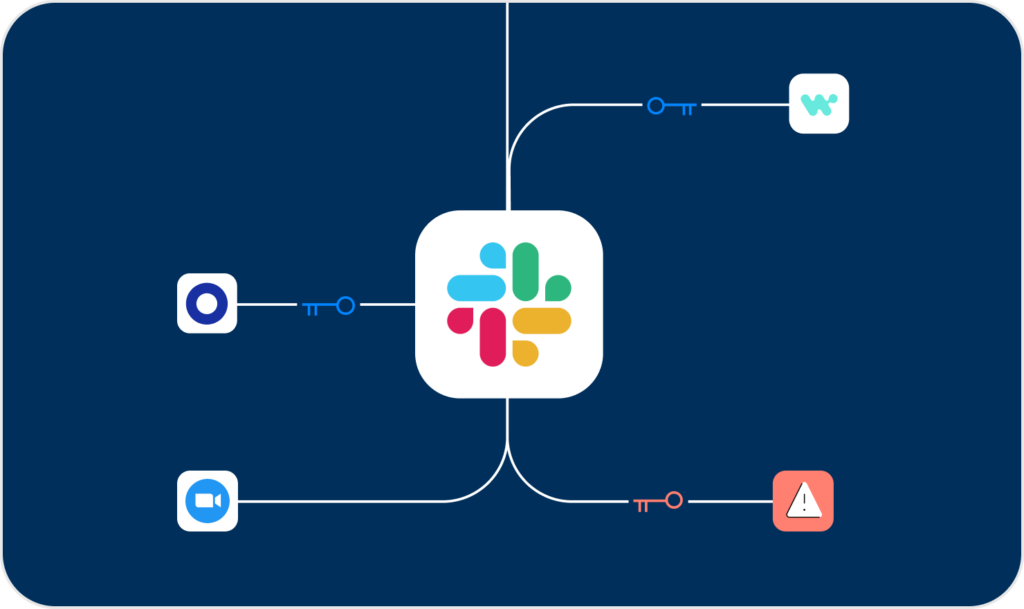
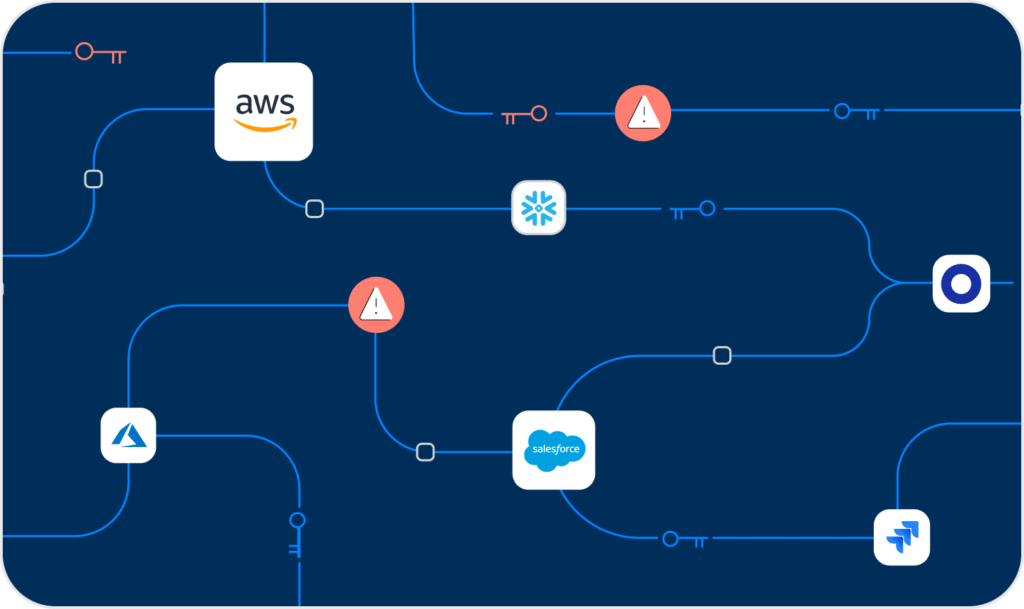
Get a complete and up-to-date inventory of all internal & third-party non-human identities in your environments. See their associated risk, vendors, business value, and owners in one place.
Continuous NHI mapping
We secure NHIs across IaaS, SaaS, PaaS, and On-Prem environments
From AWS, Azure, GitHub and BigQuery to Salesforce and Office365, we ensure your environments are protected from NHI risks.

FEATURED
Why machine credentials are your biggest blindspot
Non-human identities are a wild west of ungoverned access. But what are they? How can you monitor them? and why should you care?