13 non-human identity attacks in 16 months

A new generation of supply chain attacks has been rising in recent years. In such attacks, hackers abuse third-party & internal non-human identities as a means of accessing core business systems. While many conversations about supply chain security risks focus on vulnerabilities in software application components themselves, or in their human-to-app connections, they overlook a critical area of supply chain security risk: non-human identities and their ungoverned access to core business and engineering environments.
The threat is real: A new generation of supply chain attacks
Security issues related to app-to-app connections are not theoretical. A variety of recent incidents highlight the risk posed by insecure non-human access:
- 𝐈𝐧𝐭𝐞𝐫𝐧𝐞𝐭 𝐀𝐫𝐜𝐡𝐢𝐯𝐞 𝐛𝐫𝐞𝐚𝐜𝐡 (Oct 2024): 𝐨𝐧𝐞 𝐀𝐏𝐈 𝐤𝐞𝐲 𝐞𝐱𝐩𝐨𝐬𝐞𝐝 1 𝐦𝐢𝐥𝐥𝐢𝐨𝐧 𝐬𝐮𝐩𝐩𝐨𝐫𝐭 𝐭𝐢𝐜𝐤𝐞𝐭𝐬 . thousands of Internet Archive users with support tickets received a follow-up message revealing that an exposed API key was not properly rotated, allowing access to their support data.
- Massive NHI Attack (Aug 2024): Insecure AWS stored NHIs and machine credentials lead to compromise of 230 Million cloud environments.
- Gitloker (June 2024): The threat actor Gitloker exploited malicious OAuth apps to target GitHub users, causing significant data loss and ransom demands.
- JetBrains (June 2024): JetBrains found a vulnerability in their GitHub Plugin for IntelliJ IDEs, risking unauthorized access to GitHub repositories. They urged customers to revoke the plugin’s access by deleting PATs and OAuth app tokens.
- HuggingFace (June 2024): HuggingFace reported an unauthorized access to their servers, resulting in the theft of tokens and API keys from its Spaces platform.
- New York Times (June 2024): Attackers stole the New York Times’ source code by exploiting an over-privileged GitHub token, granting access to all repositories.
- Snowflake (May 2024): Hundreds of Snowflake instances were breached by the financially motivated threat actor UNC5537, affecting approximately 165 organizations.
- Dropbox Sign (May 2024): Threat actors stole customer data which included email addresses and authentication information such as API keys and OAuth tokens. Dropbox suggested rotating API keys and OAuth tokens related to this service, which include integration to Google Workspace, Office 365 and Salesforce, among others.
- Microsoft Midnight Blizzard (January 2024): Russian state-sponsored threat actors abused OAuth applications as part of their attack against the company’s corporate environment. Microsoft’s Office 365 email server was breached, and internal email correspondences of Microsoft employees’ were exposed.
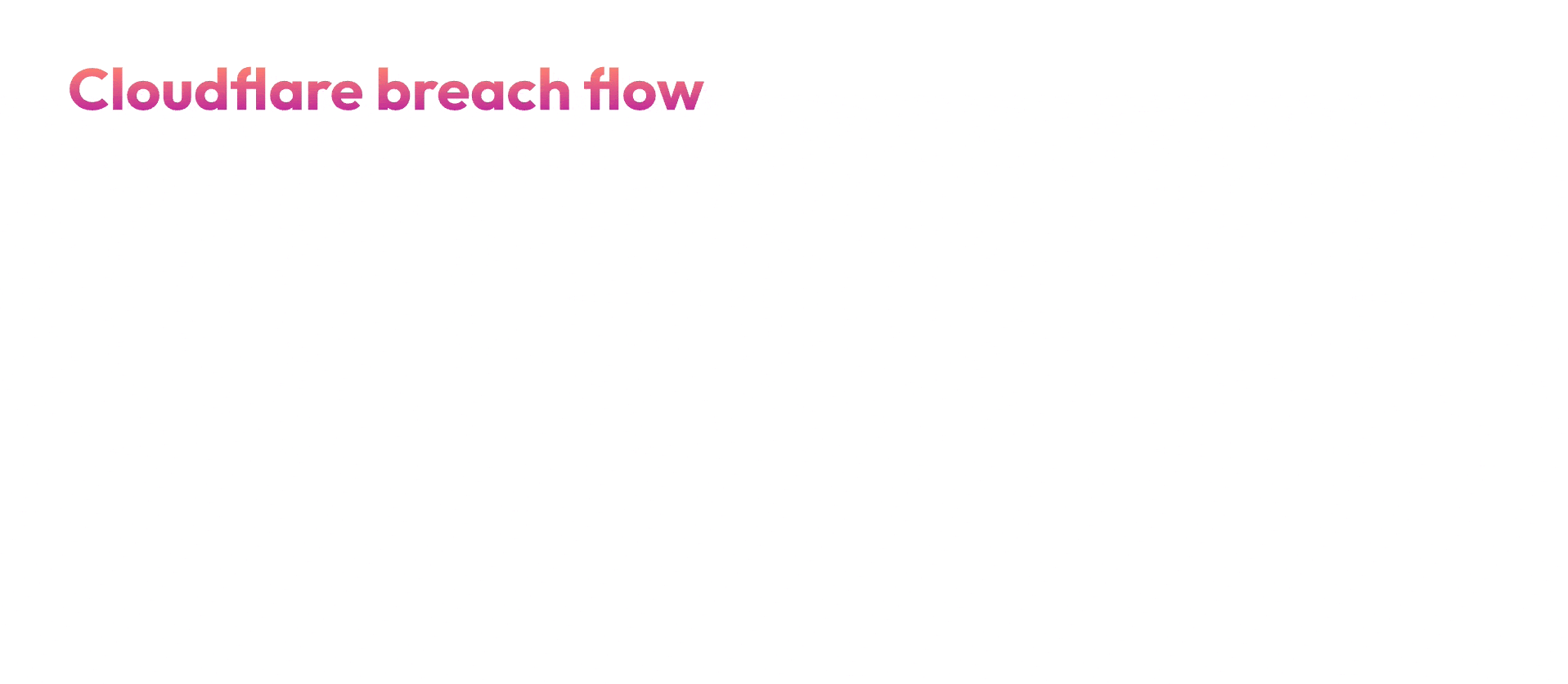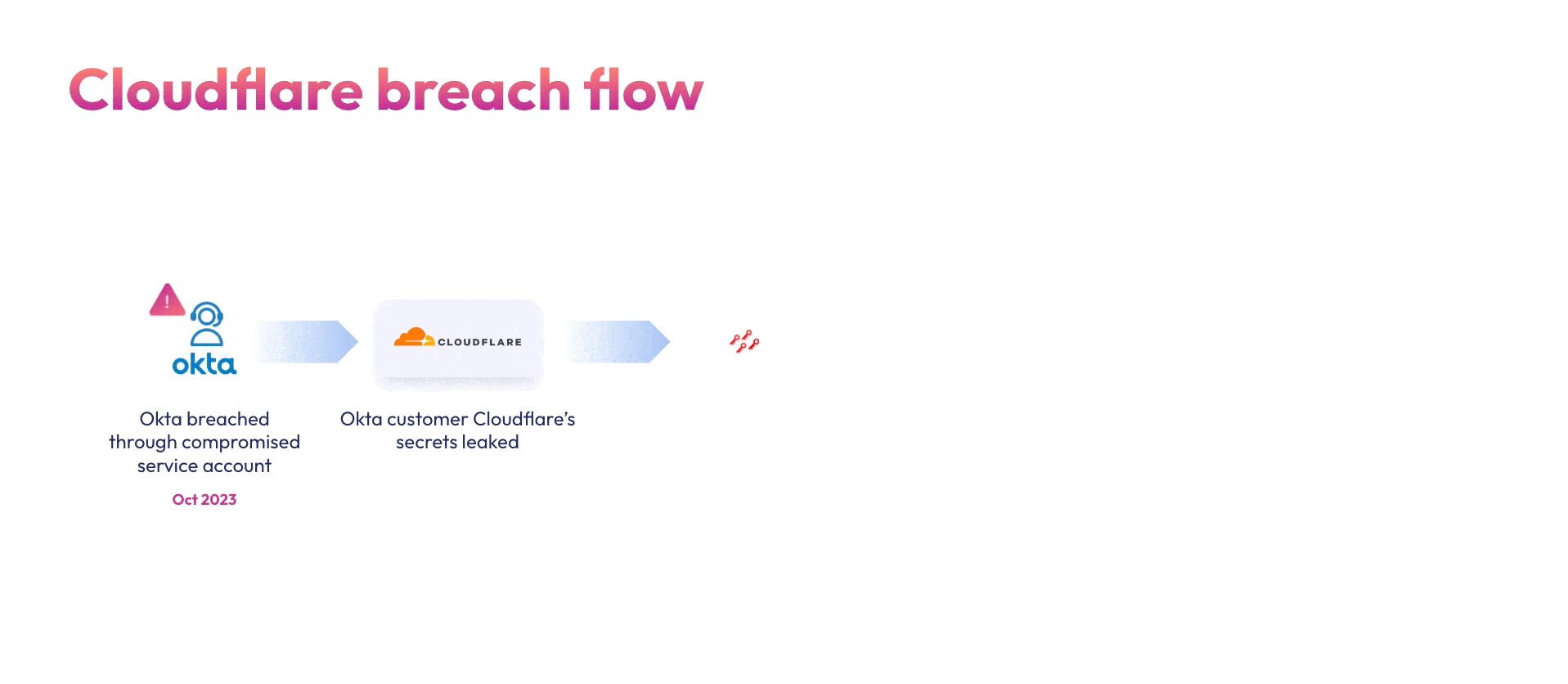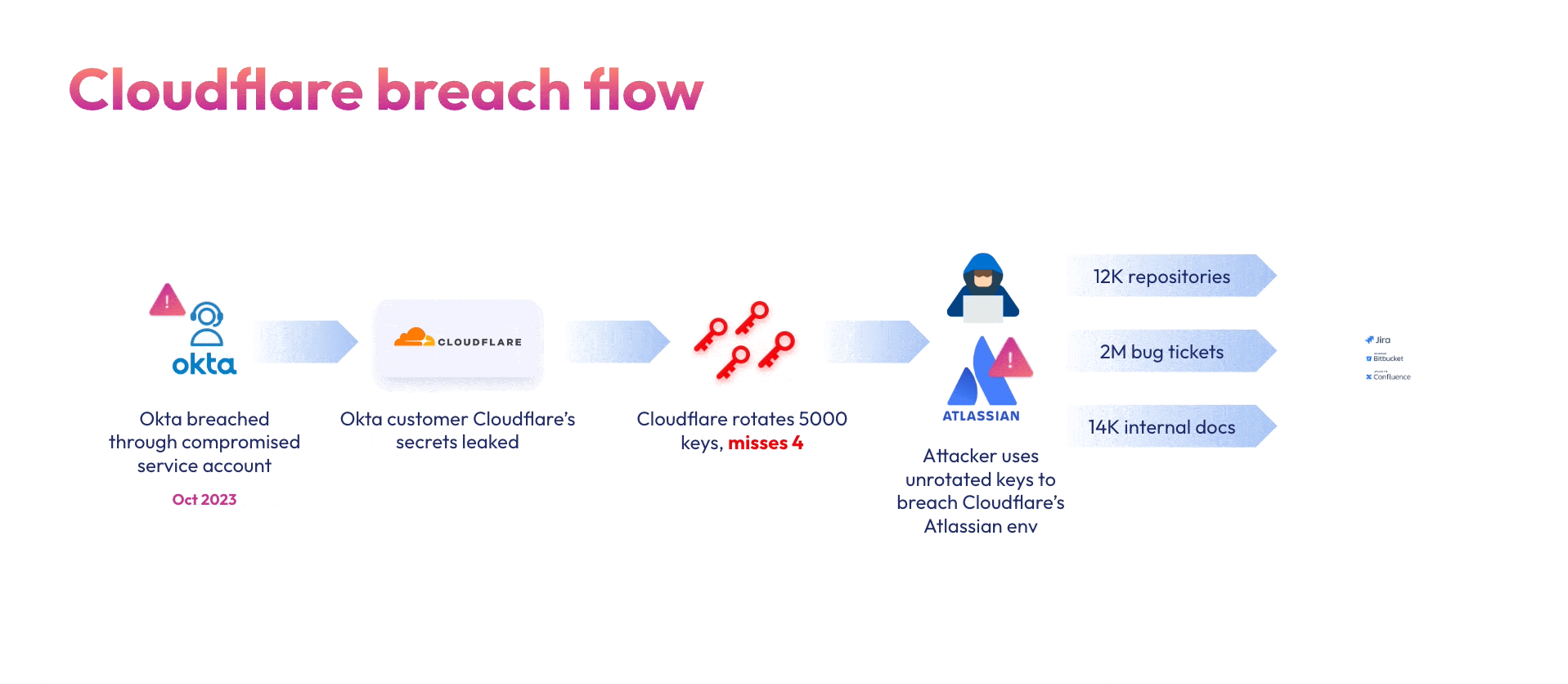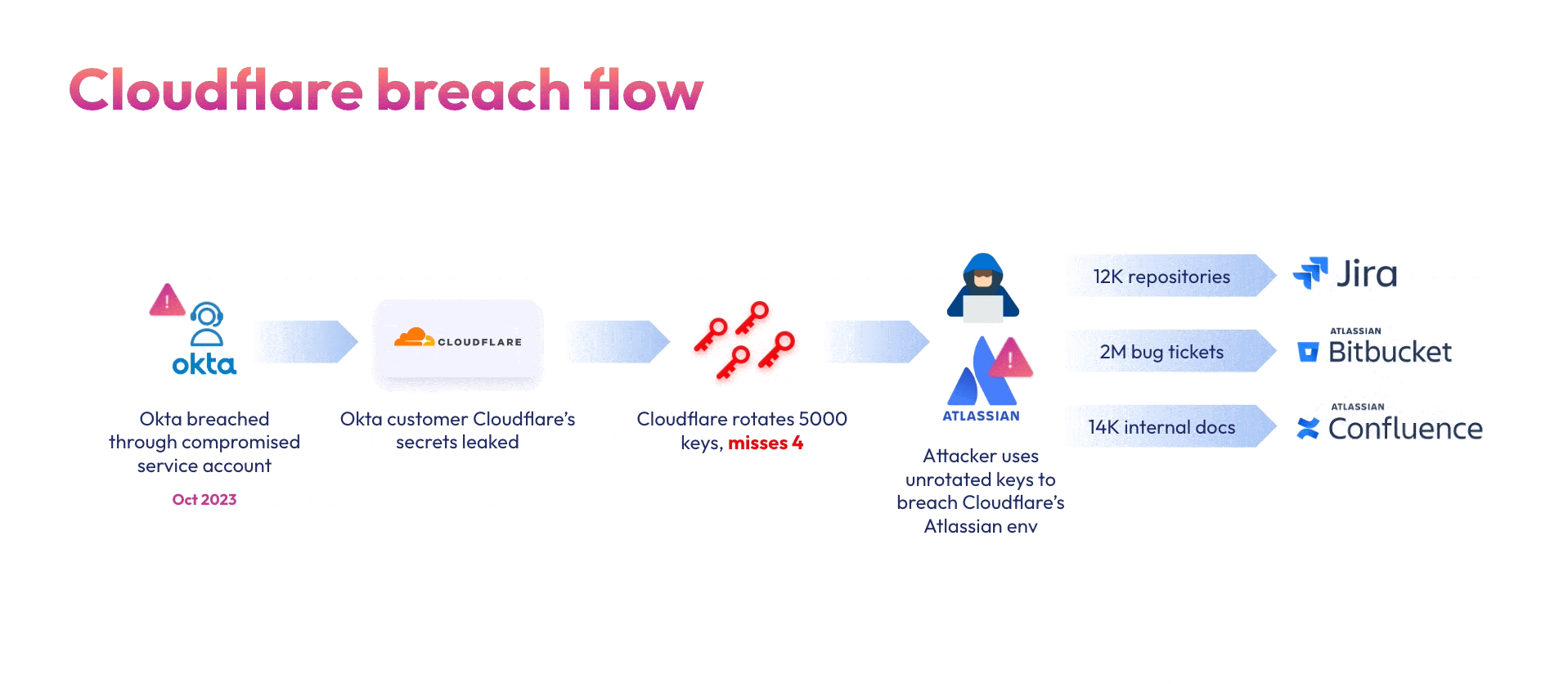
- Cloudflare (November 2023): Okta customer Cloudflare’s entire Atlassian suite – Bitbucket, Jira and Confluence were breached back in November 2023 due to the initial Okta breach. Although Cloudflare rotated 5000 credentials, an unrotated token and service account credentials allowed the hackers to compromise their Atlassian environment.
- Okta (October 2023): Attackers used leaked service account to access Okta’s support case management system. This allowed the attackers to view files uploaded by some Okta customers as part of recent support cases.
- GitHub Dependabot (September 2023): Hackers stole GitHub Personal Access Tokens (PAT). These tokens were then used to make unauthorized commits as Dependabot to both public and private GitHub repositories.
- Microsoft SAS Key (September 2023): A SAS token that was published by Microsoft’s AI researchers actually granted full access to the entire Storage account it was created on, leading to a leak of over 38TB of extremely sensitive information. These permissions were exposed to attackers for over 2 years.
- Microsoft365 Forged Access Token (July 2023): Inactive signing key was stolen from a possibly breached enterprise Azure system, and used to sign and create valid email access tokens, which were erroneously accepted by the Azure AD cloud system of several of its customers. This allowed the hackers to expand their reach to Office365 used by all organizations sharing the same Azure AD cloud environment.
- Jumpcloud (July 2023): During an ongoing investigation of a breach, Jumpcloud invalidated all API keys and later urged its customers to rotate all tokens provided.
- WordPress Ultimate Member plugin (July 2023): A critical vulnerability enabled full takeover of a WebPress website exploiting the vulnerable plugin, allowing any unauthenticated attacker to create users with full, administrative permission at will.
- Slack GitHub Repositories (January 2023): In this incident, threat actors gained access to Slack’s externally hosted GitHub repositories via a “limited” number of stolen Slack employee tokens. From there, they were able to download private code repositories.
- CircleCI (January 2023): In this attack, engineering employees’ computer, which was compromised by malware that bypassed their antivirus solution. The compromised machine allowed the threat actors to access and steal session tokens. Stolen session tokens give threat actors the same access as the account owner, even when the accounts are protected with two factor authentication.
- GitHub Personal Access Token (December 2022): On December 6, 2022, repositories from GitHub’s atom, desktop, and other deprecated GitHub-owned organizations were cloned by a compromised Personal Access Token (PAT) associated with a machine account. The malicious actor then used the PATs to read these repositories, which contained sensitive information.
- Microsoft OAuth Phishing Attack (December 2022): Malicious OAuth apps were used to steal customers’ emails. The threat actors then used these accounts to register verified OAuth apps in Azure AD for consent phishing attacks targeting corporate users in the UK and Ireland.
- Microsoft OAuth (September 2022): By exploiting OAuth integrations, malicious applications were deployed on compromised cloud tenants. From there, they modified Exchange Online settings to spread spam.
- GitHub (April 2022): Stolen OAuth tokens allowed attackers to breach dozens of GitHub accounts, using Travis CI and Heroku as backdoors.
- Mailchimp (April 2022): Hackers misused API keys to breach hundreds of Mailchimp accounts.
- Codecov (April 2021): One attack path the attackers took was to steal git access tokens of 17,000 companies from Codecov and use them to access private Git repositories and compromise sensitive data (see an example of this attack against Twilio company in image A below).
This list could go on. Other big-name companies affected by attacks wherein hackers abused identities or access keys include Slack, Microsoft and Google.
What is causing the spike in supply chain attacks?
Securing human access via IAM tools is no longer enough. These days, every employee delegates access, on average, to ten third-party cloud services and Gen-AI tools to automate tasks and increase efficiency. This sprawl of third party non-human access to core systems (such as Salesforce, GitHub, Microsoft 365) via service accounts, OAuth tokens, API keys, etc., creates an ungoverned attack surface.
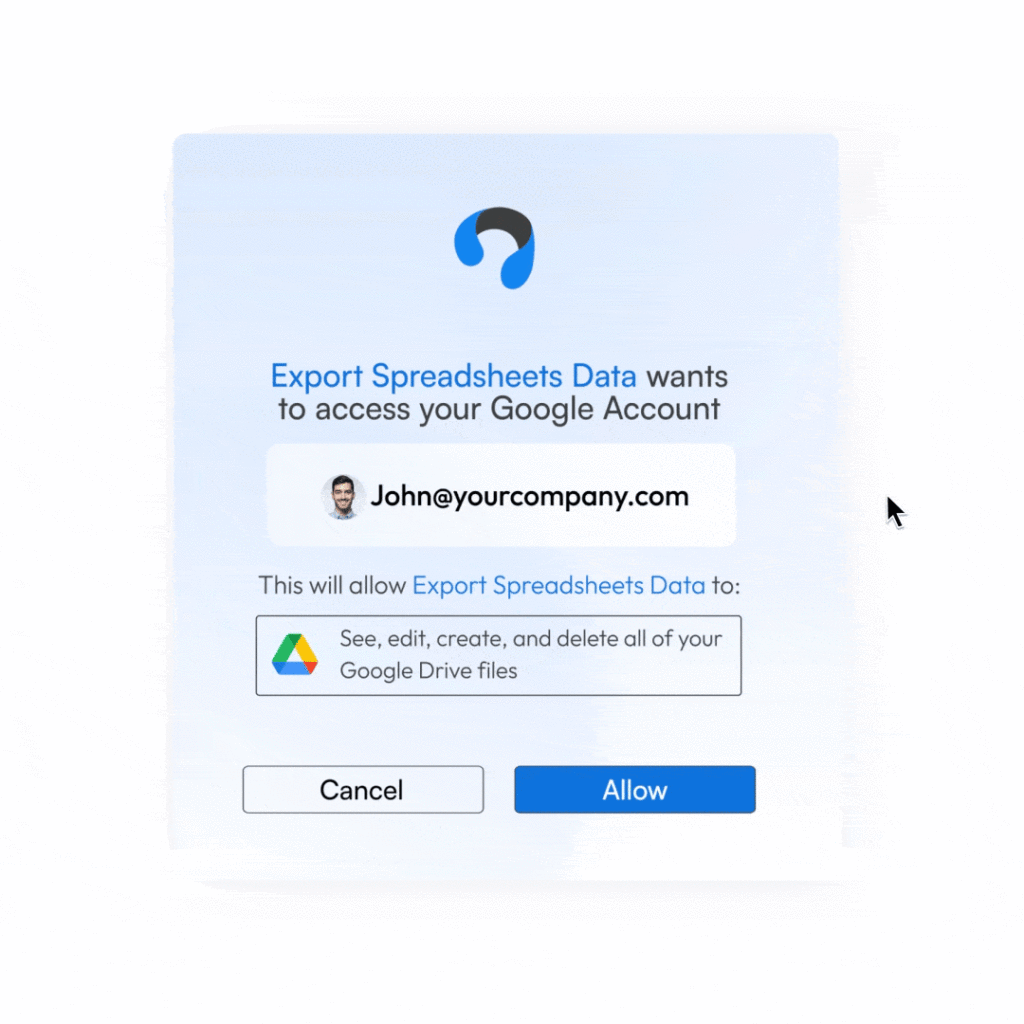
To make matters worse, internal services and resources connected via secrets are created and scattered all over by R&D teams that are not responsible for securing them, with zero visibility for security teams, and existing solutions are not built to solve these problems. Vaults only store your secrets without any context like secret risk severity or usage insight, and secret scanners only find exposed secrets, again without any context.
Think about these daily scenarios:
- An engineering team lead using a new cloud-based dev productivity tool that relies on API access to your source code repositories.
- A marketing operations manager trialing a new SaaS prospecting tool – and integrating it directly with your Salesforce instance to sync leads automatically.
- A software engineer sends a teammate an access secret for an internal IT Slack Bot app so they can investigate a bug together
Improperly secured non-human access, both external and internal, massively increases the likelihood of supply chain attacks, data breaches, and compliance violations, as recent attacks reveal. In these attacks, attackers take advantage of the access granted to third-party and internal cloud services as a backdoor into the companies’ most sensitive core systems.
Non-human identity attacks frequency and intensity will increase
Unfortunately, the size and scale of the problem is only worsening. Here are 3 of the major reasons for this:
- Business app environment – With core systems like Slack offering at least 2,000 integrations in their marketplace alone, ‘non-technical’ employees can freely connect third-party apps to these core systems. These ‘non-technical’ employees usually lack cybersecurity awareness, and therefore may unknowingly connect untrusted, over-privileged, and later unused third-party apps to their accounts.
- Engineering environment – IT teams, DevOps and others are increasingly providing API-based access to third-party applications from core systems like GitHub or Snowflake. These shadow integrations (created using API keys, service accounts, webhooks, OAuth tokens, or even just SSH keys) create another whole ecosystem of supply chain dependencies.
- Low-code/no-code platforms – Tools like Zapier, Workato and Microsoft Power Apps are allowing “citizen developers” to integrate and automate processes with a flip of a switch. The ease with which these tools enable anyone to create advanced integrations between critical systems and third-party apps amplifies the web of tangled app integrations even more. In fact, the threat posed by these platforms is so great that analyst firm Forrester believes we will see a major breach in 2023.
Why security solutions fall short
If you look at how third-party app integrations typically work, and the level of visibility that businesses have into them, it’s not hard to understand why hackers would focus on exploiting supply chains. We live in a world of “extended enterprises,” meaning that organizations rely heavily on third-party app integrations. For example, the average enterprise employs about 1400 cloud-based apps, generating even more integrations.
And simply keeping track of all of these integrations is a huge task. User Access Management solutions (such as Okta, Auth0, and Cisco Duo) and Cloud Access Security Broker (CASB) platforms focus solely on securing user credentials and user-to-application connections. They do not monitor and govern non-human identities and ensure core systems are securely connected to third party cloud services.
API keys, OAuth apps, webhooks and any other NHIs are powerful credentials and should be protected as vigorously as user passwords. Leaking an API key can be more consequential than leaking a username and password login since logins are often protected by two-factor authentication nowadays, whereas API keys are not.
The Astrix approach to supply chain security
By automatically creating an inventory of non-human identities that access enterprise environments, whether engineering or business environments like GifHub, Salesforce and M365, then detecting over-privileged, unnecessary or malicious integrations, you can find and mitigate supply chain risks. And you can do it without disrupting the ability of your business users to deploy the integrations they need to remain productive.
At Astrix, we’ve built a solution that does just that. Using an agentless approach, we provide comprehensive visibility into non-human identities across all SaaS, PaaS and IaaS environments. We allow businesses to identify their non-human access, detect risks, remediate gaps and manage the complete NHI lifecycle to prevent new risks from arising.
This means that businesses can take full advantage of the power of automation and connectivity without compromising on security.
Contact us to learn more about how Astrix can help protect all layers of your supply chain.