
Bridging the NHI security gap: Astrix and Torq partner up
Discover, secure and manage AI agents & NHIs
Maintain real-time inventory of all AI agents, MCP servers, and NHIs, with context to understand risk and business usage.
Identify and remediate AI agents and NHIs with excessive privileges, vulnerable configurations, abnormal activity, and policy violations.
Provision secure-by-design AI agents with short-lived credentials, just-in-time, precisely scoped access, and policy at creation.
Set policy to resolve hygiene issues, reduce attack surfaces and prevent compliance violations.
Manage AI agents and their NHIs from provisioning to decommissioning.
Detect and respond to threats such as compromised credentials and out-of scope agent actions.
Control and enforce policies across your NHI attack surface.
Manage NHIs from provisioning to decommissioning.
Detect and respond to suspicious NHI activity & 3rd party breaches.
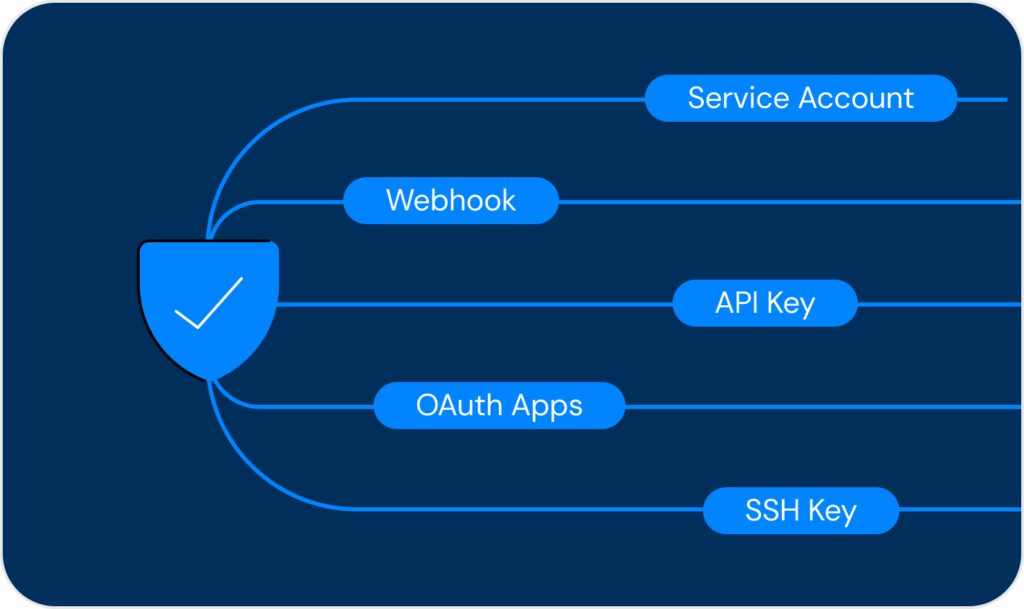
Centralized secret management across vaults & cloud.
Discover and assess third-party apps & vendors accessing your environment
The latest on AI agent & NHI threats, products stories and more
Meet Astrix at industry leading events
Watch on-demand sessions and expert insights
The latest company announcements and press
How our customers secure their NHIs with Astrix
Latest reports and whitepapers about NHI security
What is Agentic AI and related NHI risks
Core concepts, functional components, and technical capabilities
What are they & common vulnerabilities
How attackers exploit them & how to prevent it
The risks they pose & how to secure them
Definition, common use, and why they're important to secure

Danielle Guetta is the Director of Product Marketing at Astrix Security, where she crafts compelling go‑to‑market strategies for the fast‑growing domain of non‑human identity (NHI) security. With a knack for storytelling and data-driven campaigns, she led the launch of Astrix’s groundbreaking Cloud Security Alliance report—gathering insights from 800+ cybersecurity pros—and has since championed its thought leadership in the market
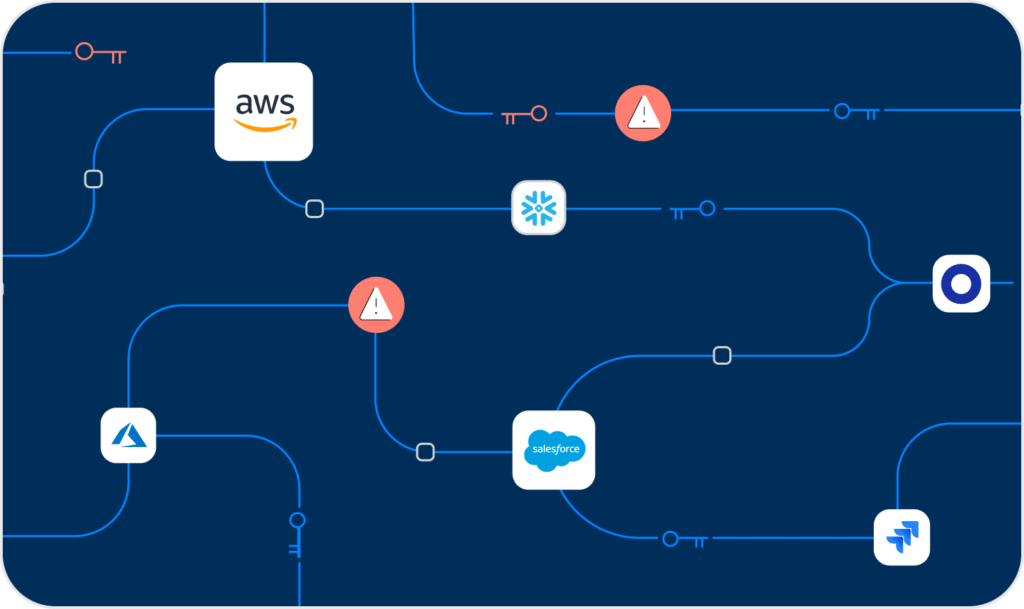
Not just code vulnerabilities: The overlooked cause of software supply chain attacks

Looking Back at Our Journey in the 2023 RSA Innovation Sandbox Contest

Security Magazine – Non-human identities: Secure them now, not later


Forbes – Shadow Connections: How They’re Impacting Your Production Environment And Software Supply Chain Security
