AI Agent Security
Discover, secure, and deploy AI agents responsibly across the enterprise
AI Agents + NHIs > Humans
Secure the Identities that Matter
99% of identities are ungoverned
Agents and NHIs outnumber humans 100:1, yet remain outside IAM and audit review cycles.
Overprivileged agents
Employees grant agents NHIs with broad — often static — permissions to corporate assets.
No trace or accountability
While operating autonomously — many remain shadow agents, without clear human ownership.
Agentic & Non-Human Identities
Discover. Secure. Deploy.
Discover
A single inventory of AI agents and Non-Human Identities (NHIs), with the context you need to understand risk and business usage.
Automated discovery of all agents—custom, third-party, or home-grown—including shadow, unregistered agents.
Secure
Identify and remediate AI agents and NHIs with excessive privileges, vulnerable configurations, abnormal activity, and policy violations.
Deploy
Deploy ‘secure by design’ AI agents with least-privileged access policies and full audit trails.
Provision agents with short-lived credentials, just-in-time, and precisely scoped access only to what’s required.
Why Astrix
We help you realize the value of AI agents faster- by mitigating risk earlier
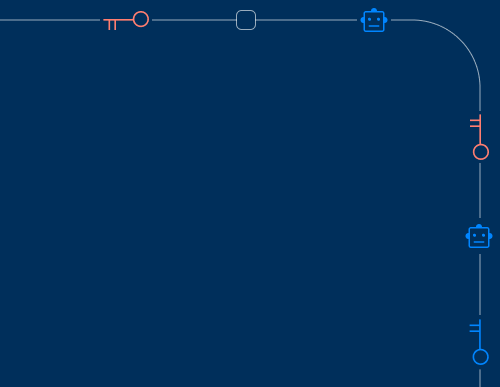
Meet you where you are
Our Discover–Secure–Deploy framework gets you agentic-ready. Gain visibility first, set access security guardrails, and move confidently to secure agent deployment – ready for rapid scale.
One solution for NHI & AI agents
Instead of juggling multiple tools, Astrix enables you to close the most urgent identity security gaps—NHI and AI agents— with a single platform.
Tackle agentic risks at the source — IAM
OWASP stated clearly: “NHIs play a key role in agentic AI security” since they define precisely what your AI agents can and cannot do. To secure agents, you must start with access. And to secure access, you must secure their NHIs. There’s no way around it.
Experts in next-gen identities
Since 2021, Astrix has pioneered and defined NHI security—helping Fortune 1,000 enterprises extend traditional IAM to cover NHIs. Backed by deep research, real-world experience, and mature technology, Astrix is uniquely positioned to secure AI agents better than any other solution.
FEEDBACK
Trusted by industry leaders
Learn more
Start securing Agentic identities today
See how we can help you discover, secure and deploy AI Agents & NHIs